A hazard of cloud-based services is reputation hijacking — using the cover of a legitimate cloud service to do bad things. For example, you can’t block the domain “Google.com”, because it has legitimate purposes. So a network administrator is left in a difficult quandrary.
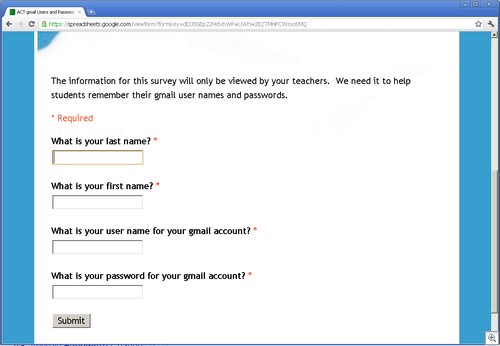
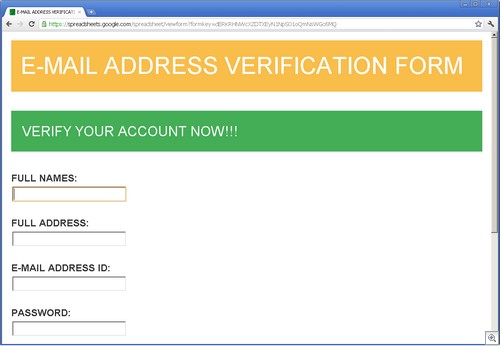
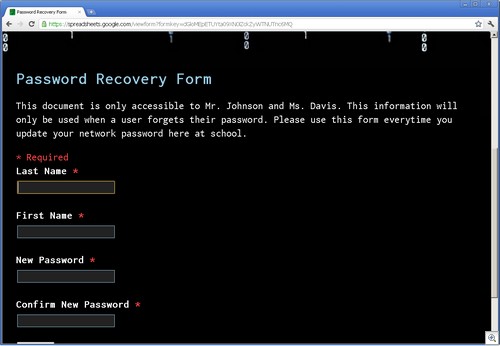
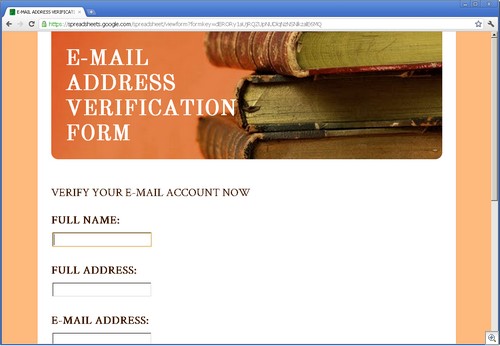
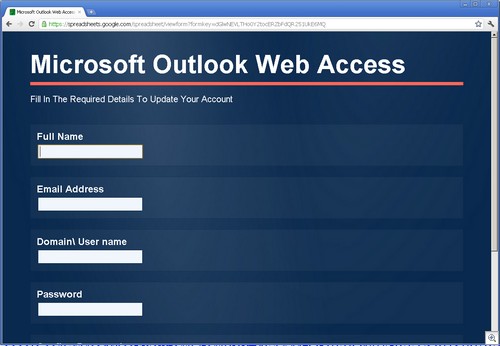
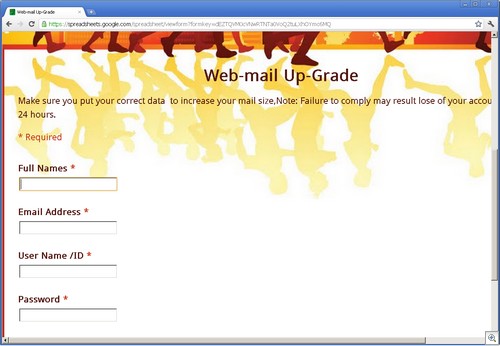
As an example, Google Docs (specifically, Spreadsheets), is a playpen for phishers. We have found a very large number of phishing sites using Spreadsheets, especially for stealing credentials.
These phishing sites all use the ability of Google Spreadsheets to create forms. These Google forms have wonderful legitimate uses, such as empowering teachers with the ability to collect data from students. But their ease of creation makes for a dangerous situation.
Since all of these forms use the “formkey” parameter in the URL, searching for them is trivial, using a simple google search like this one.
Schools are a particular target, but it’s not limited to just that area.
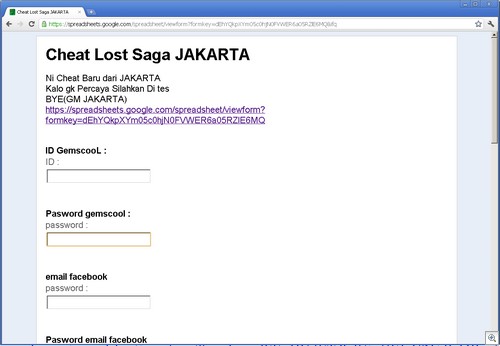
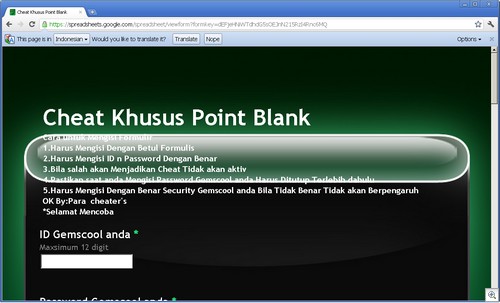
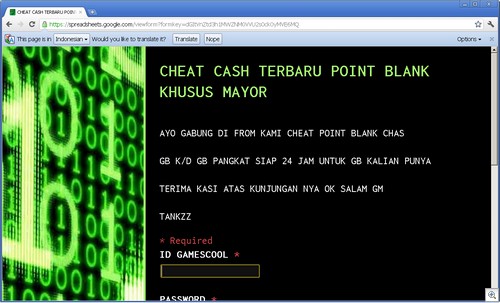
One major area of popularity for this use is in Indonesia, where these phishing sites are setup to steal credentials for various games. Gemscool (an Indonesian gaming site) is a particular target, such as for the Point Blank (PB) and Lost Saga games.
Some examples:
If it only takes a simple Google search to find these, one wonders exactly why these aren’t being policed more aggressively. This is trivial stuff to find.
Alex Eckelberry
(With thanks to Sonny Discini)