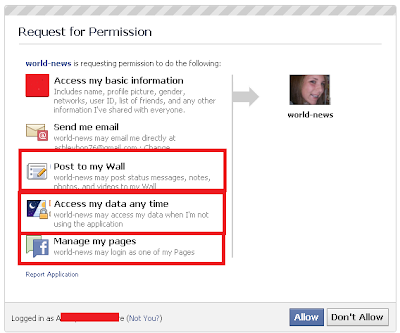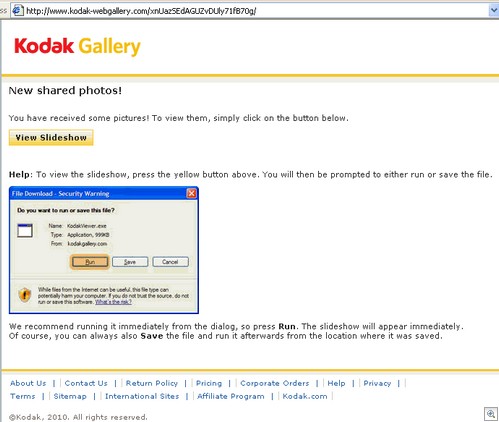
Above, you can see a vaguely optimistic VirusTotal user summary in relation to a file that’s been doing the rounds for about a month or two. Here is the file in question:

A “receipt generator”, I hear you ask – what do people want with one of those?
The answer, of course, is rather straightforward:
This is a particularly interesting scam, as it doesn’t target regular PC users – it targets the people who sell you things, such as the merchants on the Amazon marketplace. This is what the would-be social engineer sees when they fire up the program:
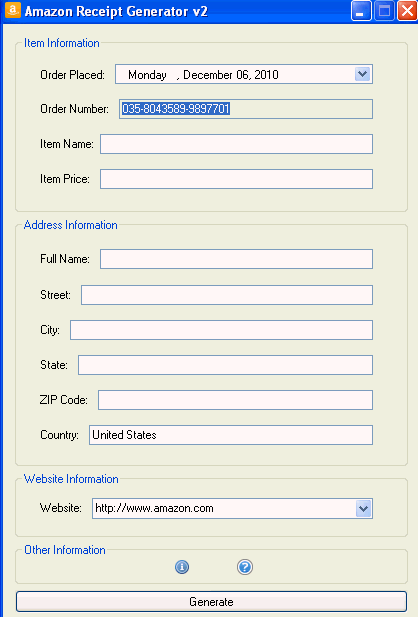
They can fill in a variety of information, including Item name, Price and the date the order was taken. Additionally, it allows them to choose between the .com, .co.uk, .fr and .ca Amazon portals. When they hit “Generate”, a html file is created in the program folder which looks like this:
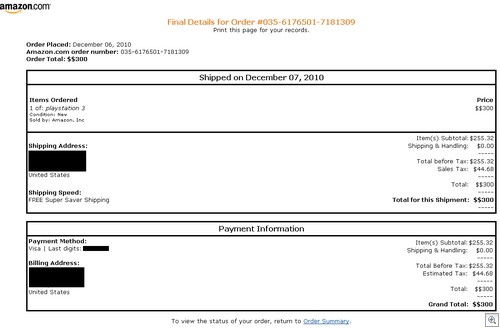
Click to Enlarge
It’s a pretty good facsimile of a genuine Amazon receipt – I just logged into my Amazon account, hit the “Printable Order Summary” button on an old order and it’s identical to the above. Note the small details, such as “Total before tax”, “Sales tax” and other touches that make it as convincing as possible.
What happens once our scammer is armed with his fake receipt? Well, many sellers on Amazon will ask you to send them a copy of your receipt should you run into trouble, have orders go missing, lose your license key for a piece of software and so on. The gag here is that the scammer is relying on the seller not checking the details and accepting the printout at face value. After all, how many sellers would be aware somebody went to the trouble of creating a fake receipt generator in the first place?
Some things to note for the wary seller: not only will you not have a record of these people buying your products, you should be able to confirm with Amazon that no purchase was ever made. Check the orange order number at the top, because those are randomly selected from a set of looping numbers every time the scammer clicks on the “Order Number” button – again, something either the seller or Amazon should be able to check. Finally, the program seems to add some random digits on the “Visa: payment method” section in payment information.
As you can see, the careful seller has little to worry about – many of the items in the fake printout are convincing as a whole, but once you start digging into the details a little bit it quickly falls apart. However, it seems this program has started a little wave of imitations, as evidenced by this screenshot lifted from a (now defunct) downloads portal:
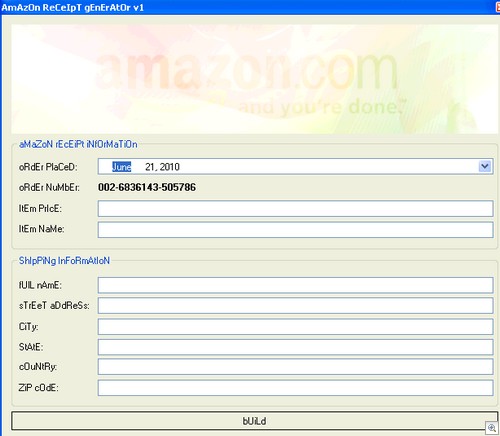
Click to Enlarge
Oh dear.
Anyway, it’s clear that sellers will need to keep their wits about them over the coming festive season as I can see this being a particularly popular scam for the time being. If a “customer” seems a little peculiar, ensure you take a good look at their receipt – you probably don’t want to have a Homer Simpson moment after you’ve sent three Playstations to their dropoff address.
We’ve passed the files onto Amazon, and the VirusTotal detection rate is currently 1/42 – we detect this as Hacktool.Win32.Amagen.A.
Christopher Boyd (Thanks to Adam Thomas for additional research).