Comment spam is increasing. For now, I’m staying on top of it with usually only a few hours delay. I don’t want to go to a moderated format but if it continues, I may have to.
GRRRR.
Alex Eckelberry
The Great Years: 2004-2010
Comment spam is increasing. For now, I’m staying on top of it with usually only a few hours delay. I don’t want to go to a moderated format but if it continues, I may have to.
GRRRR.
Alex Eckelberry
EMI proclaims:
“EMI is not using First 4 Internet technology. We recently completed a trial of three content-protection technologies (Macrovision’s CDS300, SunnComm’s MediaMax and SonyDADC’s key2audioXS), and First 4 Internet’s technology was not one of those tested.”
Cnet story here.
Alex Eckelberry
Based on a settlement with the Luddites, Grokster has moved offline, shutting down its service.
It’s website says:
The United States Supreme Court unanimously confirmed that using this service to trade copyrighted material is illegal. Copying copyrighted motion picture and music files using unauthorized peer-to-peer services is illegal and is prosecuted by copyright owners.
There are legal services for downloading music and movies. This service is not one of them.
Grokster hopes to have a safe and legal service available soon.
The new Grokster, called Grokster 3G, is at a new website. It promises:
A safe, secure & legal P2P experience…
NO Adware
NO Spyware
NO Bundles!
NO Viruses
NO Hassle
Just the best of what P2P has to offer.
You can signup for the beta of the new Grokster by sending an email to them.
The Luddites crow:
Mitch Bainwol, RIAA chief executive, said in a statement on Monday: “This settlement brings to a close an incredibly significant chapter in the story of digital music. At the end of the day, this is about our ability to invest in new music. An online marketplace populated by legitimate services allows us to do just that.”
MSNBC story here. Luddite propoganda here.
Alex Eckelberry
Update here.
Sony Rootkit fiasco has started one lawsuit. techdirt speculates more may be coming.
SONY IS FINALLY GOING to HAVE to answer the tough questions, it is being sued. According to the press release here, and the complaint here, the Italian group ALCEI is suing Sony over the rootkitting DRM infection. Since I don’t speak Italian(1), I will have to take the word of readers that they are doing things right.
It seems that ALCEI hired a noted Italian security researched names Stefano Zanero to dot all the I’s and cross all the T’s. This one will be great fun to watch, and hopefully will set the right precedents.
Alex Eckelberry
If you’re new to the world of home networking, this free course might be worth checking into.
This course will walk you step-by-step through setting up a secure home computer network. We assume you understand the basics of networking, so we immediately delve into more advanced topics such as advanced router configuration, custom cabling, and file sharing. We’ll discuss the advantages and disadvantages of wired versus wireless technologies, and show you how to obtain the optimum results from both. You’ll also learn how to protect your network from Internet intruders using readily available firewall software and specific router configurations.
Link here.
Alex Eckelberry
This is a local woman. What’s surprising is that the police here seem to think she was culpable. I’m not sure if they really understand the Nigerian scam business. In other words, she may be stupid but I’m not all that sure she actually understood what was happening here.
Toni Chaffer says she just wanted a job and hoped to find one in cyberspace, so she posted her resume on monster.com.
A few days later a woman from Nigeria e-mailed her with great news — an offer for a position in accounts receivable.
“Basically what she stated was that she was going to have money orders sent to me,” Chaffer said. “(She said) that her father had left her a fabric and textile business, Jeram Fabric and Textile in Nigeria, and that she had just moved over there and her father had died and left it to her in his will, and that she was just trying to get her business up and running. That she was just a single woman trying to make a living.”
…”The criminal investigation of her uttering these forged instruments will go forward and be presented to the state,” said sheriff’s office spokesman Mac McMullen. “And the state will take whatever action they deem necessary. This report has also been furnished to our economic crimes division.”
Link here.
Alex Eckelberry
(Thanks Adam)
Sunbelt Software, a leading provider of Windows security solutions, announced today it has become a member of the SecureIT Alliance. The SecureIT Alliance is an effort led by Microsoft Corporation to bring greater integration to enterprise security products, and to increase collaboration between its members for customer-driven and innovative security solutions.
The SecureIT Alliance, first announced in October by Microsoft, is dedicated to enabling participating security partners to more easily and efficiently integrate their solutions with the Microsoft platform to build innovative security features and products for the benefit of customers. As a Gold Certified ISV Partner, Sunbelt Software develops security products based on Microsoft technologies that protect enterprises against threats such as spam, spyware, and other network and system security threats.
Link here.
Alex Eckelberry
I’ve been spending some time trying to buy a laptop for my mother.
Every computer she’s ever had has been given to her as a hand-me-down. Her current PC is a tired old Compaq that I bought 10 years ago, which finally gave its last dying breath.
I lobbied my brothers for some cash and we decided to buy her an inexpensive laptop, figuring that because she lives in a condo, she is always in need of space —and more to the point, is in a continual state of bewilderment over cables, wires and hooking things up.
Her needs are very basic. She just needs a PC to connect to AOL and do her email. I wanted to get her a printer as well, and preferred a system with wifi. Most importantly, I really wanted a system with at least a 15” screen size. Finally, I felt that getting at least a 1 year service plan would be prudent.
I was tasked with shopping for a PC and decided on Dell.
That’s when things got interesting. You can find deals at Dell, but you have to really shop. The advertised deals are never good enough. You have to really dig. And one trick is to play off the Small Business website against the Home Office website. The results are surprising.
I created a basic spreadsheet, which roughly shows the differences:
| Laptop | Dept | RAM | WIFI? | Screen | Printer | Price |
| Inspiron 1200 | Home office | 256 | No | 14 | 720 basic | $587 |
| Inspiron 1200 | Small Bus | 256 | No | 15 | 924 | $712 |
| Inspiron 6000 | Small Bus | 256 | Yes | 15.4 | 924 | $739 |
| Inspiron 2200 | Small Bus | 256 | Yes | 15 | 924 | $781 |
| Inspiron 6000 | Home office | 512 | Yes | 15.4 | 720 basic | $838 |
| Inspiron 2200 | Home office | 256 | Yes | 15 | 720 basic | $874 |
These prices includes shipping, handling and tax and a one year service plan (I missed a few pennies here and there but nothing material). One odd fact is that in Home Office, Recycling is free, but costs $25 for small business.
Now, note the differences. An Inspiron 2200 in Small Business with a better printer (the 924) is over a $90 less than in Home Office. An Inspiron 6000 with a better printer (but less RAM) is about $100 less in Small Business (the difference is about $50 if you equal the RAM). The other differences are there to see.
Lesson learned: Dell is tricky in their pricing. When shopping for a personal system, really work the website and you’ll be surprised as to how much you can save. Or try the Dell Outlet — that’s what we use at the office. We’ve found that the Outlet PCs are new or practically new and you can save some money there as well (but again, you have to shop and play it against the new systems).
And you also have to look for the freebies. I almost went right by a free upgrade to a CD/DVD burner on the Inspiron 6000 — it wasn’t pre-selected!
Alex Eckelberry
From Suzi’s blog, Microsoft’s attempts at hegemony in the security space took a step forward Friday, as two Microsoft bloggers took the wraps of some product plans for “Windows Defender”, nee Microsoft Antispyware.
Not big news. It pretty much confirms what we all knew anyway. It will be part of Vista. Vista will have a security center like XP, but with the addition of an antispyware section. And there’s new news that Defender will run as a service and get its updates from Windows Update.
Steve Dodson: It is going to be a part of VISTA!
The biggest announcement we are making is that Windows Defender will be a part of Vista when it releases. You will be able to run another spyware product instead of Windows Defender if you would like. Although I may shed a small tear, you will be able to disable or turn off Windows Defender and install whichever 3rd party anti-spyware application you would like.
Jason Gams: Every week seems like a big week for us in the engineering team working on our anti-malware technology. However, last week was especially important in a sentimental way. We got the final name for the cool technology our team has been developing for Windows. The name, after long consideration by our product marketing and branding folks, is “Windows Defender”! What’s really cool about this name is that it’s more positive than “Windows AntiSpyware”. Windows Defender is about what Windows will do for customers, defending them from spyware and other unwanted software Our solution has really been about more than just the standard definition of “spyware”. We’ve always said we will provide visibility and control, as well as protection, detection and removal from other potentially unwanted software, including rootkits, keystroke loggers and more.
Alex Eckelberry
Paul Graham is one of the great thinkers and writers on the Internet. I was first introduced to his work back in 2002 with his “Plan for Spam”, where he introduced the concept of Bayesian filtering to the world. We later ended up incorporating a form of Bayesian filtering ourselves in our consumer antispam product.
He writes occasional essays on various issues related to technology, all of them interesting and thoughtful. And, as with all good writers, you may not always agree with him, but you certainly respect the thinker behind the writing.
One of latest essays, Ideas for Startups, goes into the process behind coming up with new ideas for startups. And, he recently wrote The Venture Capital Squeeze, which discusses the problems facing venture capitalists:
When we started our startup in 1995, the first three were our biggest expenses. We had to pay $5000 for the Netscape Commerce Server, the only software that then supported secure http connections. We paid $3000 for a server with a 90 MHz processor and 32 meg of memory. And we paid a PR firm about $30,000 to promote our launch.
Now you could get all three for nothing. You can get the software for free; people throw away computers more powerful than our first server; and if you make something good you can generate ten times as much traffic by word of mouth online than our first PR firm got through the print media.
Take a look, you can find the site here.
Alex Eckelberry
Pitty Viewpoint. They can’t make money. So now it appears they are expanding into adware (sort of).
According to an article in ClickZ:
Viewpoint will develop a behavioral targeting product in 2006, execs said during the company’s Q3 earnings call.
It will work by collecting clickstream data on users who have installed the Viewpoint media player, then using that data to target ads and content on the company’s partner sites. Viewpoint claims 120 million users have installed its player.
CEO Patrick Vogt announced the behavioral tech in the wake of a downbeat quarter for Viewpoint and its ad systems unit in particular, which includes Unicast. Viewpoint reported a net loss of $1.5 million on total revenue of $6 million.
Execs blamed the poor earnings on several factors, including weakness in the company’s sales and marketing organization and publisher integration problems with its new Fuse ad management platform.
Now, here’s what Viewpoint says:
AT NO TIME WHATSOEVER does the Viewpoint Media Player or the Viewpoint Manager collect ANY personal data about you or your usage patterns, nor do we install third-party software or access information on your hard drive. The auto-update process happens totally anonymously and happens solely to ensure that your player is up-to-date. Since we do not collect personal data, there is no way – as in the case of ‘spy ware’ – to “traffic” or sell your personal information. We as a company find spy ware to be reprehensible and we are committed to protecting the privacy of all of our users. Recently, we have begun offering an enhancement called the Viewpoint Toolbar to our users. This component too is designed strictly to improve the online experiences of our users and is not spy ware by any definition. The installation of this tool is completely optional and the application, once installed, does not access personal information. If a user opts-in to receive the toolbar and changes his or her mind, the component can be turned off or de-installed quite easily. We value each and every one of our users and will continue to promote innovative, next generation experiences without compromising our users’ safety, security or privacy. That is our pledge. Viewpoint Corporation
Not entirely sure what was going on, I actually listened to the conference call. It’s not entirely clear what they they will be doing, but here’s some snippets I jotted down:
Our strategy and action plan is simple. We will be expanding our current lines of business, adding one new line of business and monetizing our existing products and assets to create new revenue streams… Our search business will continue to focus on our core graphically enhanced toolbar capability…continue to make it more valuable to our users…to that end, we recently launched our Fotomat toolbar…this application provides the stickiness for our toolbar, which should increase the use of search hence generating additional revenues for our customers…
We will also, as part of the search business expansion, begin offering custom toolbars and branded browser-based applications for integration into our customers marketing plans. This will provide customers the ability to dynamically serve one-to-one marketing messaging through a persistent, permission-based marketing tool that resides right in the end-user’s browser. Reaching customers on an individual and persistent basis with compelling content is the holy grail of marketing.
Viewpoint will deliver a behavioral product in 2006 that will allow marketers to get the right message to the right customer at the right time. Behavioral-based marketing has proven to be many times more effective than traditional marketing…
“Behavioral” is often a code word for adware, but it could be simple targeted advertising based off of cookies — quite a difference. So I’m not sure I’d dump your Viewpoint player just yet. It’s not entirely clear what they will be doing in the near future, and if it will affect the player itself. We will certainly be keeping an eye on this company…
You can hear the conference call yourself by clicking here (if it’s not live yet, you’ll have to follow the insturctions in the press release.)
From ClickZ via MarketingVox
Alex Eckelberry
From ChipsPC:
The Jack-PC brings to life the unique concept of “Computer in-the-wall” fulfilling important promises to enterprise IT managers and decision makers:
Highest Applications Security
- Full Protection from Damage & Theft
- Integration with Existing Standard Enterprise Infrastructures
- Power-Over-Ethernet for the World lowest Power Desktop
Power over Ethernet (PoE) integrates power and data onto once single cabling infrastructure, eliminating the need to have AC power available at all locations.
Link here.
Alex Eckelberry
I found this to be an interesting intellectual exercise and only wish that I had more time to go into it.
You dump a bunch of nuclear waste in a special location. But how do you make sure that 10,000 years from now, someone won’t step in it?
You design a bunch of really ugly signs and earthworks.


Article here via John Murrell
Alex Eckelberry
So first we had this piece of spyware called Warden that attempts to stop players from cheating in Worlds of Warcraft.
Then we had the Sony BMG rootkit.
Now we have a potpourri. Apparently you can use the Sony rootkit to make undetectable tools to cheat Worlds of Warcraft
From Security Focus:
World of Warcraft hackers have confirmed that the hiding capabilities of Sony BMG’s content protection software can make tools made for cheating in the online world impossible to detect. The software–deemed a “rootkit” by many security experts–is shipped with tens of thousands of the record company’s music titles.
Alex Eckelberry
For online brokerage accounts. Link here.
Alex Eckelberry
(Hat tip to Funsec)
I’m currently working from home recovering from a fractured rib from a skateboarding accident. I do a style of skateboarding that is known as “vert” — going up and down ramps, that sort of thing. I, umm, kind of messed up a kick turn and took a rather nasty fall.
When I worked at Borland, Philippe Kahn had a saying that every time he went away from the company, sales went up. Hence, it is my belief that that my absence from Sunbelt will almost certainly relate to increased productivity and revenues.
There. That makes me feel better.
At any rate, Terminal Services is my best friend right now as I try and keep on top of what’s going on at the office.
Alex Eckelberry

This is very sad. From the Art of Noh blog (link here), Dmitry Zagorodniy, owner of Ukrainian National Antivirus (Unasoft) was shot dead about two weeks ago.
The blog sources an article in a Ukrainian magazine (link here). The Art of Noh has an attempted translation using Babelfish. It is a bit difficult to read, but one understands that foul play is suspected in his death and a number of disturbing events are chronicled.
To the family of Dmitry, we offer our heartfelt condolences and sincere regrets on his passing.
Alex Eckelberry
Coolwebsearch (“The Search Engine you Trust”) posted on their website a list of affiliates that have been terminated. One of them was infoglobus.com.
Coolwebsearch (aka CWS) has been fairly vehement on clearing its name, so this is of interest.
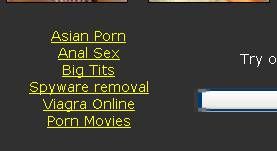
A few days ago, Senior Spyware Researcher Patrick Jordan ran across some stuff which I’m posting today as a “Seen in the Wild”.
It starts with a known CWS infester using files from another site that will hijack users to win-eto.com. The known CWS infester has links that will open to coolwebsearch.com, but it is the path it passes through before it opens Coolwebsearch.com that is unusual.
The above links show the following transmissions before opening to Coolwebsearch.com.
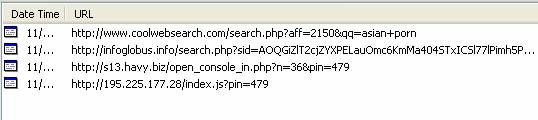
Notice the second entry: infoglobus.info.
Notice the URL: 195.225.177.28 has always been one of the IP ranges to open to Coolwebsearch.com. But the last transmission to get to Coolwebsearch.com is infoglobus.info, which uses a Coolwebsearch template that matches the one above.
Now in the hijacking page at Coolwebsearch.com we can see the entry where infoglobus.info is on the list.
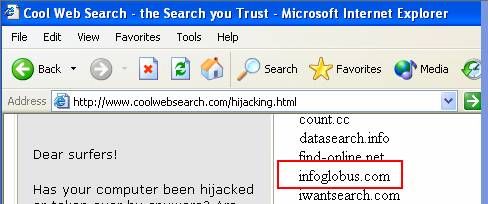
Now, infoglobus.com is listed on their website. However, infoglobus doesn’t seem to care. They just use infloglobus.info to get around the whole thing, while using a CWS template.
Tut tut tut.
Alex Eckelberry
Got this from Suzi today, a Wired article today about a guy that used botnets to perform stealth install 180 Solutions search and other adware.
In the first U.S. prosecution of its kind, FBI agents arrested a 20-year-old Los Angeles man Thursday on charges that he cracked some 400,000 Windows machines and covertly installed pop-up-generating adware on them, in a scheme that allegedly brought in $60,000 in ill-gotten profits. …
According to prosecutors, in 2004 and early 2005 Ancheta used a customized form of the “rxbot” Trojan horse program to find and take control of large collections of vulnerable PCs, spinning them into “botnets” capable of being directed as one. He then installed ad-delivery programs from two adware firms: Quebec-based Gammacash and LOUDcash, which was purchased by adware giant 180solutions and renamed ZangoCash earlier this year.
As someone pointed out to me, this particular line from 180 is a bit confusing:
“It was possible for someone to hack the notification-and-consent dialog boxes, which apparently this guy did, and subvert those so it would be installed silently,” says Sundwall.
To my knowledge, there were no notice and consent dialog boxes as he describes back in January.
Article link here via Suzi. (Btw, if you don’t subscribe to Suzi’s blog, do it — it’s outstanding).
Alex Eckelberry