A “Procedural Warning Security Alert”
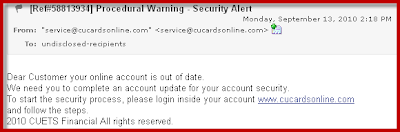
Some of the most persistent phishing schemes out there are those aimed at stealing credit card information. We got this one today. It’s aimed at Master Card Choice Rewards customers:
Your first line of defense against these things, of course, is the practice of NOT clicking on any links in email messages. Second line: if you think you’ve received a legitimate communication from your bank or credit card company, go to the web site yourself (which you might bookmark in your browser), don’t use the offered link in an email
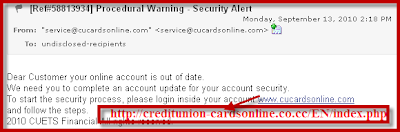
When we mouse over the link in the email, it becomes apparent that it goes somewhere else:
co.cc whois information is interesting:
Funny place for a server for a credit card security operation – the Cocos Islands near Australia — but I guess the “cc” is to make you think “credit card.”
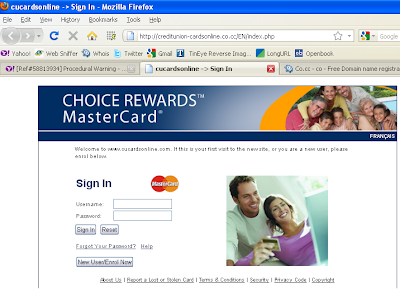
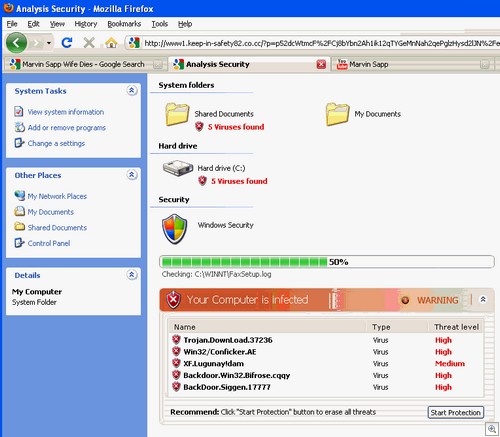
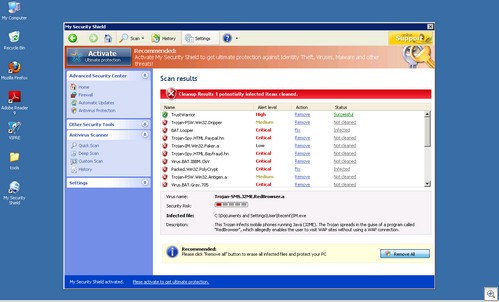
The site presents the viewer with a sign-in page, which, oddly enough, will accept ANY username and password.
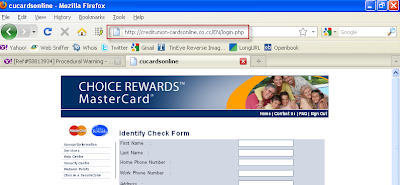
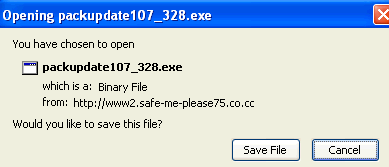
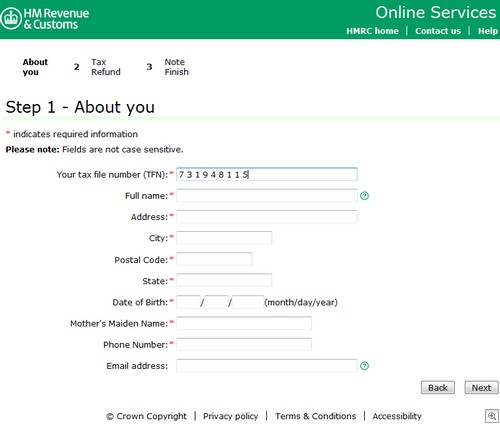
And then the real business end of the operation. An “Identity Check Form” where the malicious operators behind this beast get all the information they need to make purchases with the victim’s credit card.
This could be a creation of the individual or group behind a March phishing campaign aimed at eBay members documented by Red Condor Security company. The subject line on a phishing email they analyzed was “eBay Procedural Warning – Security Alert.”
Tom Kelchner