Dangerous search: “World Cup printable bracket”
Thanks Mike
Tom Kelchner
The Great Years: 2004-2010
Today at Tech.Ed in New Orleans, we announced plans to release two new products for the gateway: VIPRE Email Security for Gateway™ and VIPRE WebFilter™. Both products are based on a hardened Linux platform, and incorporate VIPRE technology.
These two products will be released to the public within the next 90 days.
VIPRE Email Security for Gateway provides rich antispam and antivirus functionality at the SMTP gateway. VIPRE WebFilter provides in-line content filtering and antivirus.
More propaganda here.
Alex Eckelberry
HP announced at Internet Week in New York today that it will begin making printers with their own email addresses so users can send print jobs to them from portable devices or anything connected to the web..
Vyomesh Joshi, HP executive vice president of the company’s Imaging and Printing Group, said the new Eprint service would let customers store documents in the cloud and print them with any device. He demonstrated the service using an Ipad, which has no built-in printing capability.
The Inquirer quoted, HP’s Vice President of Worldwide Marketing and Communications Tariq Hassan saying that the printer email addresses have password protecting and the process has anti-spam protection.
Inquirer story: “HP printers can get emails”
It will be interesting to see where the dark side goes with this. One can imagine malicious spam downloading malcode that will compromise the security of the printing process and set up botnets to deliver printed malvertising. Then there will be “male enhancement” and Canadian pharmacy ads waiting for you in your printer.
Tom Kelchner
Ten privacy and consumer groups have combined their efforts to seek changes in the draft privacy bill that is before the U.S. House Subcommittee on Communications, Technology and Internet. The groups released a letter today with their proposed changes.
Last month Rep. Rick Boucher (D-Virginia), who is chair of the subcommittee, and the ranking minority member of the committee, Cliff Stearns (R-Florida), introduced a draft of a bill that would expand privacy protections both on- and off-line, requiring companies to allow consumers to opt-out of any data collection. IP addresses are on the list of information covered by the bill.
Their suggestions included:
— Incorporating the Fair Information Practice Principles, including the principle of not collecting more data than is necessary for the stated purposes, limits on how long data should be retained and a right to access and correct one’s data.
— Expanding the bill’s definitions of “sensitive information” to include health-related information beyond just “medical records.”
— Requiring strict “opt-in” procedures for the collection and use of data and a prohibition on the use of any sensitive information except for the transactions that consumers provided.
Read the letter here.
News release here: “Ten Privacy and Consumer Groups Ask Congressional Leaders to Strengthen Privacy Bill“
The groups are:
— Center for Digital Democracy
— Consumer Federation of America
— Electronic Frontier Foundation
— Consumer Action
— Privacy Rights Clearinghouse
— Consumer Watchdog
— World Privacy Forum
— U.S. PIRG, the federation of state Public Interest Research Groups
— Privacy Lives
— Privacy Times
See our May 5 blog entry “Is there a privacy law in the making for the U.S.?”
After Boucher and Stearns made the draft public, consumer and industry groups quickly showed their general dissatisfaction with the draft wording, which is expected to be changed after the two congressmen collect comments. Boucher and Stearns said they hope to introduce the bill formally in coming weeks. (Our blog piece here.)
Tom Kelchner
Mark Croonen, who is the secretary of the Australian Defense Cycling Club and obviously a really serious cyclist, drew our attention to this privacy and security issue with Garmin Connect, a website on which members can upload GPS computer data from their cycling trips for others to see.
He wrote: “when you upload your ride data, by default Garmin Connect shares your data with the world unless you specifically change the privacy settings. So all things being equal the average user won’t give this a second thought and will leave the settings on public access. Furthermore even if you do change the default settings it won’t change the settings for any rides you have already uploaded, you’ll have to go back and manually change the setting for each ride.”
Croonen said the problem is that a miscreant can use the service to profile users in preparation for burglarizing their homes. Using the Garmin Connect site (without logging on), it would be possible to find riders in any area and determine what days they regularly out riding, running or whatever else they do with their Garmin GPS devices.
He said, “to a thief this is wonderful news. I’m going to guess that if you have a Garmin you’re a reasonably keen cyclist and as such you’re probably going to have a couple of bikes. (Btw I can also find out what type of Garmin you have). So I know where you live, what time you go out and how long you will be out for. Thank you the bike shop is open. As you can see from this user I just need to go around to their place on a Saturday or Sunday morning and I will have about an hour to do what I like,” he wrote.
“From here I can zoom in on their activities and see when they are out riding, walking etc. From here I can quickly look for patterns as to when the user will be out of the house and for how long.”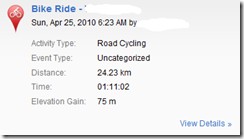
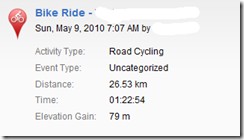
“I don’t mean to pick on Garmin Connect as I’m sure other services probably have the same issue but if you are going to use these services this is probably something you want to keep in mind.”
Mark’s discussion is “Security concerns with Garmin Connect” on his blog “The Cycle Way.”
Thanks Mark
Tom Kelchner
That is the mixed message we should take from a piece of spam floating around mailboxes over the weekend.

Click to Enlarge
I suppose it should be no surprise that with everyone sweating over whether or not to cancel their Facebook accounts, spammers should jump on the bandwagon and pretend you’re never going to see your farm or fortune cookie applications again.
“You have deactivated your Facebook account. You can reactivate your account at any time by logging into Facebook using your old login email and password. You will be able to use the site like you used to”.
Thank goodness for that! Anyway, clicking the Signin button takes you to a cookie cutter pharmacy site hosted at oursharp(dot)com:
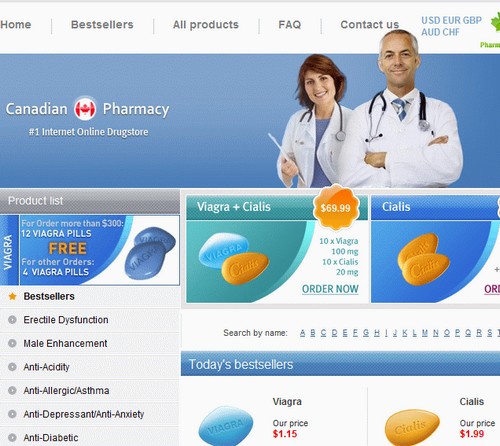
I’m almost certain I didn’t add a “Cheap Viagra” application onto my Facebook page recently, but I suppose I could be wrong. I’m just glad they didn’t have the brainwave to direct users to a phishing page – I suspect if that had been the case, it might have taken considerably longer to tell me how many cows you have on Farmville…
Christopher Boyd
Slightly more time gaming than the average U.S. citizen watches TV
Marketing research firm NPD Group studied the gaming habits of 20,000 members of its consumer panel and found that the most avid group spends 48.5 hours per week playing computer games.
The study divided gamers into six groups. The most intense group, the “extreme gamers:”
— averaged 29 years old
— were mostly men (although one third were women!)
— played mostly on consoles
— purchased 24 games in the previous three months
— make up only four percent of the 174 million people who play computer games in the U.S.
The study also found that the average time spent playing games grew from 12.3 hours per week last year to 13 this year.
Study: ‘Extreme Gamers’ play 48 hours a week
Computers and computerized equipment have massively changed life in one generation and stories like this are snapshots of those changes. You can draw a lot of conclusions from the facts, ranging from “That isn’t healthy! Why don’t they go outside and play?” to “Whoa! What a market!”
Here’s a whole different slant though. Our own Chris Boyd has made a career out of the gaming he loves. This is his take:
“I think I probably fall at the extreme end, probably clocking up somewhere between 5 to 8 hours a day gaming. I also use that time to explore console based exploits, scams and other shenanigans so hey, it’s all for the greater good.
“I’d also add that if it wasn’t for computer games (wow, remember when people still called them that?) I might not be working with tech or computers now. The Commodore Plus/4 blew me away when I realized I could program crude text adventure games on it, and the fun of pulling both machine and game apart continues to stay with me today. If I couldn’t have played games on it, I’d have probably used it as a doorstop and ended up selling double glazing or something.
“Also, the Dreamcast was the best console of all time.”
Tom Kelchner and Chris Boyd
Tom Baker was the best Doctor. Now that we’ve got that out of the way, you may have heard the BBC has created a downloadable Doctor Who game called “City of the Daleks”. It seems they released it early, but the game has caused a bit of an outcry. See if you can guess why from the EULA screenshot:
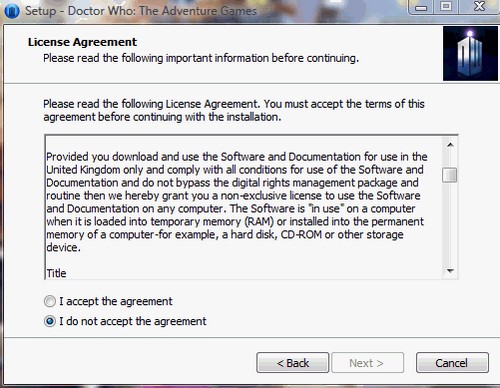
“Provided you download and use the software for use in the United Kingdom only…” That’s right, because the game is funded by the licence fee anyone in the UK can get it for “free”, but it’s currently unavailable to anyone outside that region – paid versions will be released at some point in the near future.
Of course, this hasn’t gone down too well with people seeing the below screen when trying to download:
All manner of proxies, tricks and mirrors have been deployed in an effort to get around the geolocational locking used to prevent non UK residents playing the game, which has also apparently resulted in people having a fiddle with program files to disable the protection.
This means in a short space of time numerous versions of the game are springing up to download, some of which seem to be legit:
However, there are many others out there with different file sizes, filenames or both.
Some sites are advertising downloads on Youtube, then going offline completely the next day like the site below did:
While they appeared to be linking to a file showing up as the correct download size (by itself not an indicator of legitimacy), there are others out there which seem to have gained a fair few MBs:
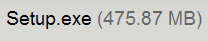
475MB? Shouldn’t that be 331MB? Also note that the name of the file has changed from “Installer-CityoftheDaleks.exe” to “Setup.exe”. I haven’t been able to grab the above file for inspection as it seems to be taking a bit of a hammering download wise, but I’d advise anyone desperate to grab a copy of the game from Rapidshare, Mediafire or anywhere else (there’s quite a few filesharing forums distributing copies of the game, too) to please be careful and scan with an antivirus program before running it.
DON’T follow the advice on this forum and “disable AV software” if trying to install copies of the game obtained from sources other than the official page, especially if you’re dealing with a random file you just grabbed from some site you’ve never heard of.
There are some things even the mighty sonic screwdriver can’t fix, and your PC is probably one of them.
Christopher Boyd
/ Edit 1 – Someone has even uploaded a version to a site that requires payment by SMS to obtain the gamefile, to the tune of £10 plus network rates. That’s pretty spectacular.
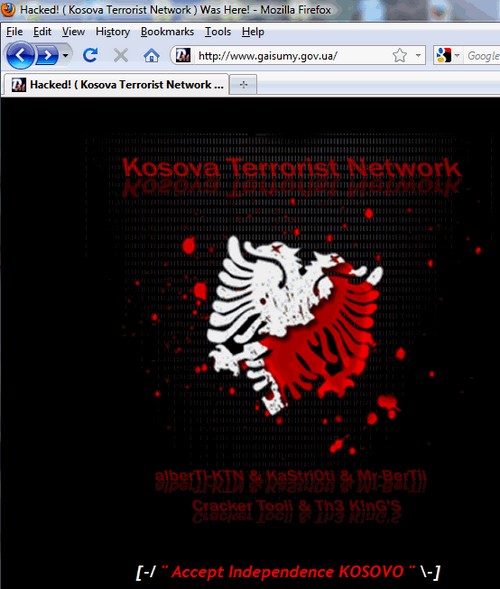
Defacing a .gov.ua website that seems to have something to do with law enforcement / traffic policing and putting the words “Terrorist Network” on the splashpage?
Yeah, that’s going to end well.
Christopher Boyd
Microsoft has issued an advance notification for patch Tuesday next week. There will be:
— Six bulletins affecting Windows (two critical, four important)
— Two affecting Microsoft Office (important)
— One affecting Windows and office (important)
— One affecting Internet Explorer (critical)
Jerry Bryant, Group Manager of Response Communications also said Microsoft will be acting on two Security Advisories:
— closing Security Advisory 983438 (Vulnerability in Microsoft SharePoint Could Allow Elevation of Privilege) with the June bulletins.
— addressing Security Advisory 980088 (Vulnerability in Internet Explorer Could Allow Information Disclosure).
June 2010 Security Bulletin Advance Notification here.
Tom Kelchner
Well-known predictor of the future Gartner is advising enterprises to start installing and testing Windows 7 this year and try to finish replacement of Windows XP by the end of 2012.
Microsoft will continue to support WinXP until April 2014, however, by the end of 2012 many newer applications written by independent vendors will not support XP, they said.
Michael Silver, a Gartner vice president, said: “In various Gartner polls and surveys, 80 percent of respondents report skipping Windows Vista. With Windows XP getting older and Windows 8 nowhere in sight, organizations need to be planning their migrations to Windows 7. Windows 7 has been getting positive reviews, and many clients report that they have plans to start their production deployments, but there are some that are still undecided about when to start and how quickly to do the migration.”
“Organizations wanting to do as much of the migration as possible though PC refresh or attrition, should begin by deciding on a start date,” according to Steve Kleynhans, Gartner research VP.
News release here: “Gartner Says Most Organizations Should Be Planning and Testing Windows 7 in 2010 and Try Eliminating Windows XP by End of 2012”
Tom Kelchner
Objective-C has been pegged as the tenth most-used computer language in the world, according to the TIOBE Programming Community Index.
TIOBE wrote: “Despite the fact that Objective-C only gained 0.08% last month, it has entered the top 10 for the first time. This is quite an achievement, especially if one bears in mind that only 13 different programming languages had a top 10 score since the start of the TIOBE index in June 2001. The main (and probably only) reason for Objective-C’s popularity is that it is the only language in which you can write applications for the iPhone or iPad. From a programming language point of view, Objective-C (born in 1986) offers no new interesting features.”
Index here.
I think it is safe to say that we’re going to see the growth of exploits (Trojans?) written in Objective-C and exploits targeting applications written in Objective-C. The target, of course will be iPhones and iPads and other devices that use apps created in Objective-C.
TIOBE says its name is an acronym for ‘The Importance Of Being Earnest,’ taken from the comic play written by Oscar Wilde in the 1890s. The site says: “By choosing this name, the founders of TIOBE Software emphasize their sincere and professional attitude towards customers, suppliers and colleagues.”
If you’ve ever read or seen the play, that name could hint at a wild and crazy corporate culture. The play is pretty whacky and Oscar Wilde was timelessly over-the-top funny.
Tom Kelchner
The U.S. Federal Trade Commission has reached a settlement with CyberSpy Software, LLC, of Orlando, Fla., that requires that company to rewrite its keylogging software to give warning when it is being installed on a computer and stop a number of illegal practices.
The FTC in 2008 brought an action against CyberSpy that advertised its product as a “100% undetectable” way to “Spy on Anyone. From Anywhere.” The company provided the software to customers with instructions on how to send it to a victim disguised as another file which would secretly install the application. RemoteSpy then monitored key strokes and sent the information to a web site where the customer could download it.
According to the FTC: “The final Order bars the defendants from providing purchasers with the means to disguise the product as an innocent file or e-mail attachment. It also requires that they inform purchasers that improper use of the software may violate state or federal law. The final Order also requires the defendants to take measures to reduce the risk that their spyware is misused, encrypt data transmitted over the Internet, police their affiliates to ensure they comply with the order, and remove legacy versions of the software from computers on which it was previously installed.”
The order was entered in the U.S. District Court for the Middle District of Florida.
FTC news release here.
RemoteSpy has been in VIPRE detections since 2005. It can log chat conversations, keystrokes, website visited, application usage, windows viewed and documents opened
Tom Kelchner
Security firm Intego has found a downloader for spyware being installed by a number of applications and screen savers from download sites including MacUpdate, VersionTracker and Softpedia. The name: OSX/OpinionSpy.
Intego researchers said they found the malcode in the MishInc FLV To Mp3 media converter and screensavers created by 7art-screensavers:
Secret Land ScreenSaver v.2.8
Color Therapy Clock ScreenSaver v.2.8
7art Foliage Clock ScreenSaver v.2.8
Nature Harmony Clock ScreenSaver v.2.8
Fiesta Clock ScreenSaver v.2.8
Fractal Sun Clock ScreenSaver v.2.8
Full Moon Clock ScreenSaver v.2.8
Sky Flight Clock ScreenSaverv.2.8
Sunny Bubbles Clock ScreenSaver v.2.9
Everlasting Flowering Clock ScreenSaver v.2.8
Magic Forest Clock ScreenSaver v.2.8
Freezelight Clock ScreenSaver v.2.9
Precious Stone Clock ScreenSaver v.2.8
Silver Snow Clock ScreenSaver v.2.8
Water Color Clock ScreenSaver v.2.8
Love Dance Clock ScreenSaver v.2.8
Galaxy Rhythm Clock ScreenSaver v.2.8
7art Eternal Love Clock ScreenSaver v.2.8
Fire Element Clock ScreenSaver v.2.8
Water Element Clock ScreenSaver v.2.8
Emerald Clock ScreenSaver v.2.8
Radiating Clock ScreenSaver v.2.8
Rocket Clock ScreenSaver v.2.8
Serenity Clock ScreenSaver v.2.8
Gravity Free Clock ScreenSaver v.2.8
Crystal Clock ScreenSaver v.2.6
One World Clock ScreenSaver v.2.8
Sky Watch ScreenSaver v.2.8
Lighthouse Clock ScreenSaver v.2.8
“The spyware itself is not contained in these applications, but is downloaded during the installation process,” they said.
“The information provided with some of these applications contains a misleading text that users must accept explaining that a ‘market research’ program is installed with them, but not all of these specify this. Some of these programs are also distributed directly from developers’ web sites with no such warning.
“The malware, a version of which has existed for Windows since 2008, claims to collect browsing and purchasing information that is used in market reports.”
In reality it installs a backdoor (port 8254); injects code into Safari, Firefox and iChat; finds personal data and transmits it in encoded form.
Intego blog here.
Paul Ducklin at Sophos AV dug in to the malcode a bit further – running one of the 7art screen savers. The app was bundled with something called PremierOpinion from VoiceFive Inc. Duicklin found that VoiceFive had the same address in Reston, Va., as notorious spyware distributor comScore. That group delivered spyware named MarketScore several years ago. Ducklin also found that the 7art domain was registered in Moscow, Russia.
Ducklin blog here.
Tom Kelchner
Five facing federal indictments in banking Trojan theft
Five alleged money mules have been indicted in federal District Court for the Eastern District of North Carolina in connection with the illegal May 2007 transfer of $450,000 from the bank account of the city of Carson, Calif. The cash was transferred after a banking Trojan (Talex) infected the computer of the city treasurer Karen Avilla. All but $44,000 was recovered.
According to the indictment, Jennifer Ann Woodard, Deago Larase Smith, Lance Corbett Holt, John L. Quinn II and Anthony Leonard Bobbitt will face federal charges of bank and communications fraud.
Indictment here.
Softpedia news story here.
There have been very few prosecutions of money mules, who are mostly recruited through work-from-home schemes. The mules provide organized crime groups in other countries with details of their bank accounts. The malicious operators, using banking Trojans, tap the bank accounts of their victims and transfer cash to the mules, who take a percentage. The mules then use untraceable wire transfers to send the money to the criminals out of the country.
On one hand, the mules can claim they were duped, but on the other hand the descriptions of the jobs they take are pretty suspicious to anyone with half a brain. They end up being the lynch pin in a process that siphons hundreds of millions of dollars from corporations, organizations and government groups.
Last month, the head of the FBI’s Cyber Crime section, Patrick Carney, told a Federal Deposit Insurance Corporation symposium in Arlington, Va., that the Bureau was planning to pursue the mules:
“We want to make sure that public understands this is illegal activity and one of the best ways we can think of to give that message is to have some prosecutions. We realize it’s not going to make the problem go away, but it should help raise awareness and send a signal,” he said.
Brian Krebs column: “FBI Promises Action Against Money Mules”
Tom Kelchner
The U.S. Federal Communication Commission has launched a program to give consumers software tools to test the speeds of their broadband services.
The commission is offering two tools, Ookla and M-Lab (both still in beta) that will test broadband services by transferring a temporary file and measuring performance of providers’ services.
The FCC-supplied tools will test:
“Download Speed: The speed at which data is sent from the testing server to your computer.
“Upload Speed: The speed at which data is sent from your computer to the testing server.
“Latency: The time it takes for data to be sent from your computer to the testing server and back (the ‘round trip time”’).
“Jitter: The variability in the delay between your computer and the testing server.”
The commission said “This beta version is the FCC’s first attempt at providing Americans with real-time information about their broadband connection quality. The FCC will continue to explore ways to improve user experience and the feature sets of these tests.”
Info here: “About the Consumer Broadband Test (Beta)”
Tom Kelchner
“Anyone else getting this crap today?”
Alert reader David McSpadden notified Sunbelt of the following spear-phishing attempt that was sent to users, appearing to come from their system administrator. [The PDF contains a link to the executable for the user to download.]
“If you already received this information before and action has been taken, then please ignore.
“This important information about a security vulnerability requires your immediate attention!
“All systems detected using Adobe products have been sent out this e-mail and are all requested to update their systems urgently.
“Kindly follow the instructions in the e-mail as forwarded below.
“Failure to comply will result in all financial and non financial loss to be a liability of the receiver.
“Please treat this e-mail as a matter of urgency. No further follow up warning will be sent.
“**This e-mail is a computer generated e-mail from admin@xxxx.com and does not require a reply**
“— On Fri, 5/28/10, Rxxxxxx Bxxxxxx <rbxxxxx@adobe.com> wrote: —
From: Rxxxxxx Bxxxxxx <rbxxxxx@adobe.com>
To: Administrator <admin@xxxx.com>
Subject: Adobe Security Update
Date: Friday, May 28, 2010, 11:24 AM
“Broadcast message:
“Adobe has issued a directive which states that all systems running their software should be patched for the latest security glitch.
The CVE-2010-0193 Denial of Service Vulnerability has recently been discovered on several systems running the previously released version of the software, which has been further documented on security sites such as http://www.securityfocus.com/bid/39524
It is strongly advised that all systems running the Adobe software is updated with the latest security patch to avoid further situations hampering the security and integrity of the system. Failure to follow the directive would mean that any loss which occurs due to the negligence will be a liability of the company and not Adobe. The link to update the system with the latest patch and instructions are provided below:
“Download the instructions here: hxxp://190.144.101.204/adobe/update.pdf (requires Adobe Acrobat Reader).
To update your system, download the installation file here: hxxp://190.144.101.204/adobe/adbp932b.exe (adbp932b.exe).
(Read first the instructions before updating the system)
“Your urgent attention is most appreciated,
“Rxxxxxx Bxxxxxx
Adobe Risk Management
xxx Park Avenue
San Jose, CA 95xxx-xxxx
Tel: xxx-xxx-3932
xxxxxx@adobe.com”
The executable tries to inject code into explorer.exe under the guise of an Adobe update (including a phony license agreement, below):
The main file is a self extracting EXE that drops code in TempIXP000.TMP as UNINST~2.EXE.
It has been associated with the iframedollars (rogue security product) primary downloader and about six other secondary’s which were first found in April. VIPRE detects it as Trojan.Win32.Generic.pak!cobra. Only seven out of 41 anti-virus products on Virus Total detect it.
Trojan.Win32.Generic.pak!cobra was the third most common detection in May according to Sunbelt’s ThreatNet statistics.
Thanks David, Patrick and Dodi
Tom Kelchner
If you like gunning down cowboys in the Wild West – and who doesn’t – then you may well have picked up Red Dead Redemption over the last couple of weeks, especially given that it’s one of the highest ranking games in years.
One of the most interesting aspects of the game is the treasure hunt, where you use cryptic clues and drawings to find landmarks in the gameworld to get your hands on bars of gold.
All in all, it’s a rather entertaining task. The problem is that there are plenty of opportunities to get stuck while looking for these bars of gold, and it seems the Rogue AV peddlers are living up to their reputation as no good pesky varmints.
A basic Google search for “Red Dead Treasure Map” gives us these three sites as the top results:
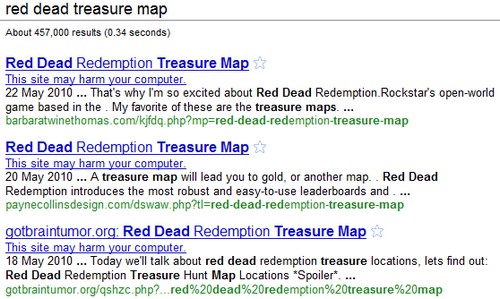
While the sites are flagged in Google for harming your computer, you can of course find these sites (and many more besides) riding high in other search engines too which means a potential lack of a warning message in Search results, and also a lack of warning if you’re using a browser that doesn’t have built in alerts.
Here’s a typical report for one of the sites mentioned – as you can see, it’s Rogue AV links all the way. While the last time the site mentioned in the report served malware was just yesterday (and a number of the sites are already being cleaned up) there are many links out there with around 25 potentially dangerous links in the first eight pages of Google alone.
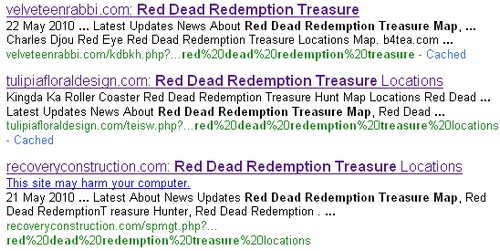
Should the unwary user click into the middle link for example, they’ll find their browser minimises to a single prompt telling them their PC is “infected”, and when they hit OK they’ll see this:
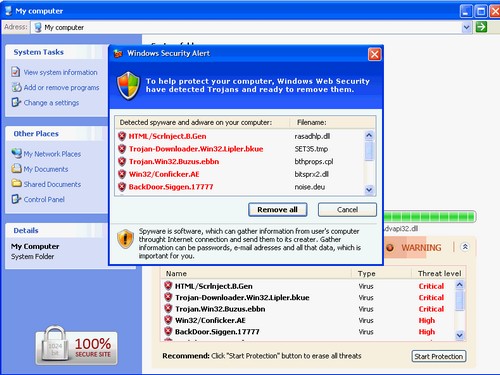
We know from experience that no end of people will download and install the fake security software from these sites, and unfortunately many more will pay to unlock the completely useless “full version” into the bargain. Cue desktop looking like this:
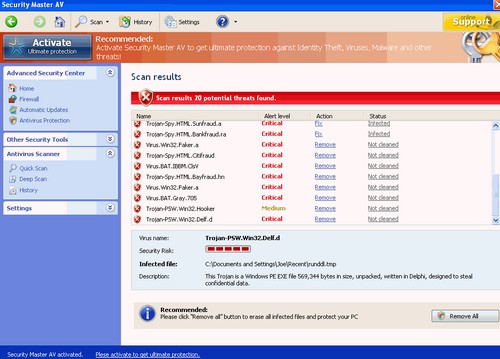
At that point, I believe the chap in the stovepipe hat and the tape measure will do you a good deal on a wooden coffin. We haven’t seen other aspects of the game targeted by this Blackhat SEO campaign yet, but that doesn’t mean it won’t happen. Be on your guard and keep your six shooters ready…
Christopher Boyd
You might want to avoid the temptation to download and run a program being touted on Youtube as a Modern Warfare 2 Cheat Console, which I’ve seen spammed to a couple of gaming forums and a bunch of video sharing websites. Here’s one of the videos in question currently advertising it:
No surprises here that it’s actually a malicious program, and will drop a file called server.exe into your Application Data folder:
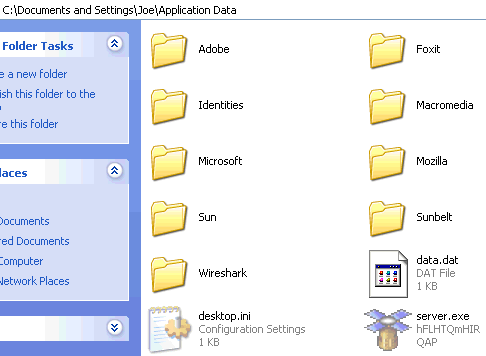
From there, endless calls go out to furz(dot)no-ip(dot)biz, although it’s currently out of action so whatever grand plan the creator had in mind isn’t currently materialising. Of course, the no-ip URL could come back to life at some point so it’s probably best not to get too complacent. VirusTotal detections were showing as 7/41 a day or two ago, but it’s gone up slightly to 13.
We detect this as Trojan.Win32.Generic!BT.
Christopher Boyd