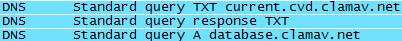Not too long ago, a relative of mine fell for a Rogue AV “pay up to get your computer back to full health” scam, handing over $69 / £45 in the process.
Whoops.
After a bit of a clean up and some silliness with the credit card company (who originally told them they couldn’t get their money back – not true), all was well again. However – it occured to me that despite having read something in the region of six million Rogue AV blogposts (and counting), I’d never actually seen the really basic stuff. You know, emails they send you once you’ve paid up. Support pages, things like that. Did support portals even exist for Rogue AV programs?
Honestly, I had no clue.
I suppose that’s because our primary function when a Rogue AV hits is to tell you what the scam is, then advise to steer clear. The only way we could show you those things is if someone we know managed to get tangled up in one of these fiascos.
Well, step forward helpful family member and bring your scam trophies along for the ride. If you ever wanted to see a “Congratulations, you just bought nothing” email then you’ve come to the right place:
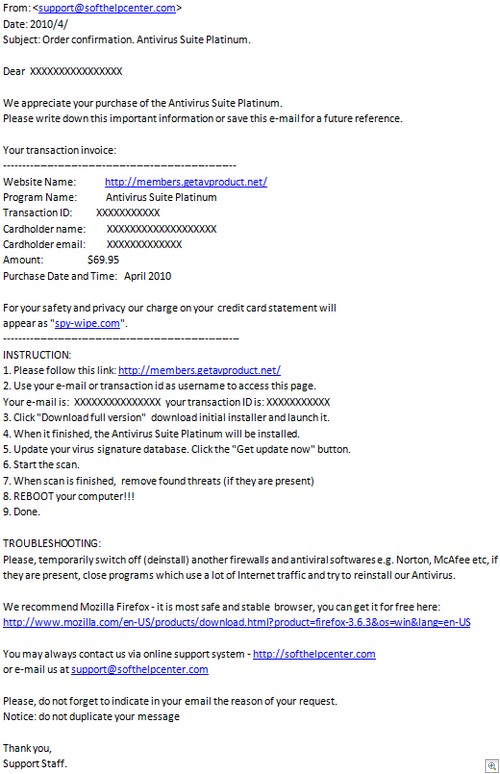
Click to Enlarge
I like the part where they advise you to remove and / or switch off Firewalls and other security products. I can imagine a regular end-user being somewhat baffled by this mail – already, a number of domains are thrown at them.
They list the reason for showing the card charges from “Spy-wipe(dot)com” as being for YOUR “safety and privacy”. Softhelpcenter(dot)com directs you to an E-Ticketing system, and the link which allows the end-user to grab their purchased product – members(dot)getavproduct(dot)net – is unsurprisingly bland and content free:
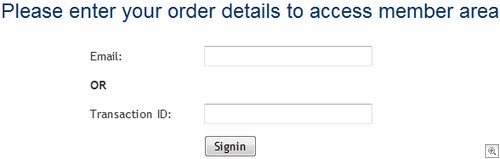
I was very curious at this point – would the login page actually take me to a support section? Or was it non functional? The answer is: here comes a bunch of screenshots from inside a Rogue AV support section.
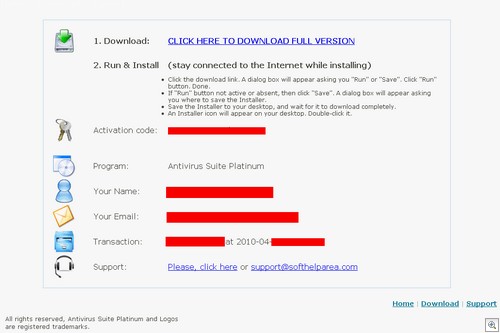
Click to Enlarge
The victim actually does get a fully functional “support” page (although truth be told, it doesn’t do much supporting). If you have a problem, the Help page is less than spectacular:
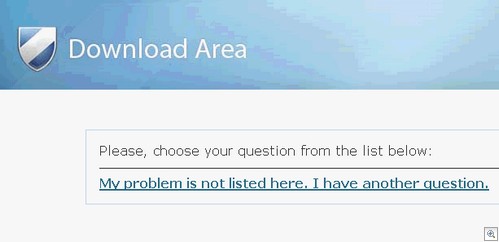
Yes, that really is the whole thing. Clicking the link will take you to a similar page to the E-Ticket site mentioned at the start of the blog entry:
One can only imagine the kinds of attachments disgruntled “customers” send them, but anyway. This is, for the record, a fully “activated” version of Antivirus Soft:
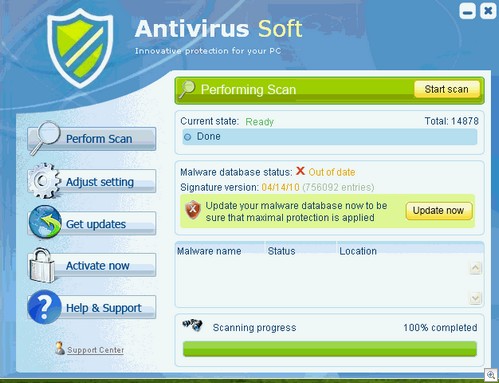
Note that it doesn’t actually look any different than the free version except for one key difference; before you pay up, your PC is supposedly infected with six thousand pieces of malware. After? Yeah, that scan is 100% finished and – amazingly –hasn’t found a single infection file.
Funny, that.
If you try to update your definitions, it performs an occasional party trick of Rogue AVs and downloads the Clam AV database.
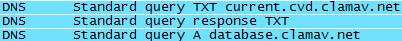
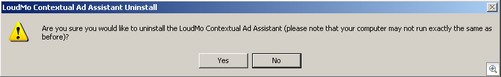
They’ll even allow you to uninstall with no apparent issues or continued nag screens:
As for the domains involved, the majority mention “Taras Frinov”, who appears in this wonderful list of rogues. While there’s a lot of identikit support sites for the end-user to download their purchase from – backsoftdownload(dot)com and getavsoft(dot)com, to name but two – it’s a better idea to not end up on these sites in the first place.
Always be suspicious when presented with popups handing out dire warnings and demanding your cash – because one “Congratulations, you just bought nothing” email is already one too many.
Christopher Boyd