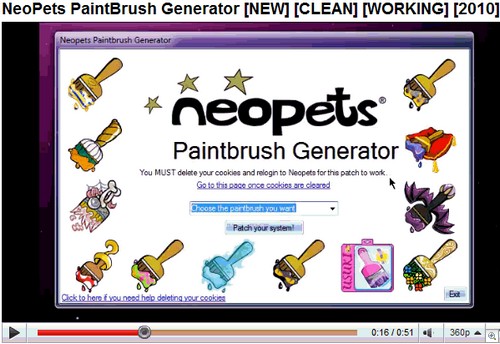
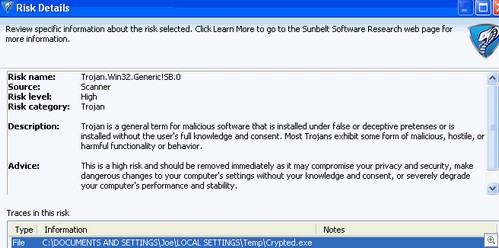
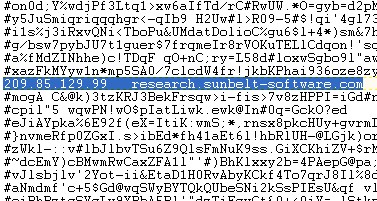
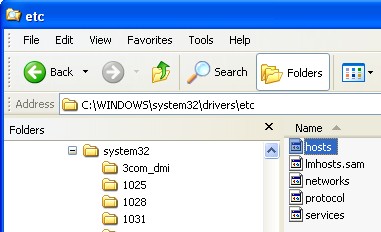
There is a risk to computer security from governments. Regulatory changes, even if they are very positive measures, can impose huge demands on an enterprise (i.e. HIPPA, Sarbanes-Oxley, California’s law requiring notification of customers whose personal information is hacked on company sites.)
The “government” risk can get no bigger than the clash of Google and the government of China over the censorship issue. The world suspects that the Chinese government or its proxies were behind a campaign of hacking against Google and other major U.S companies several months ago. Google reacted to the hacks by saying in January that it would stop censoring search results for web users in China. Monday it said it would move to Hong Kong.
The government of China, which gave the search giant the choice of censoring Internet content or leaving the country, accuses Google of being a pawn of U.S. military establishment, hell bent on subverting Chinese order – the ability of the government to protect its citizens from “harmful” Internet content.
The latest hack
Reporter Mercedes Bunz of the UK’s Guardian is reporting today that a Google web page that lists corporate executives appears to have been hacked and has been redirected to a site in China. The Guardian reported the hacks to Google staff who said they were investigating.
Story here.
(Note: see update 03/25 below)
Analysis from both sides – playing it down in China
A large volume of news analysis today quotes observers with opinions that vary from “what were they thinking, going up against the government of China?” (NYT) to “China defended itself in an ideological battle” (Peoples’ Daily Online).
China Daily reported that Chinese Foreign Ministry spokesman Qin Gang said
“The Chinese government encouraged and pushed for the openness of Internet and its management according to its laws and regulations, which was common practice in all countries.”
Story here: “Google case will not affect China-US relations”
What was Google thinking?
The New York Times quoted J. Stapleton Roy, director of the Kissinger Institute on China and the United States at the Woodrow Wilson International Center for Scholars. “I don’t understand their calculation, I do not see how Google could have concluded that they could have faced down the Chinese on a domestic censorship issue.”
Roy is a former U. S. ambassador to China.
How much is Google giving up in revenue?
The Times said some analysts estimate that Google’s annual revenue in China was only $300 to $600 million out of $24 billion in annual sales, but investors were expecting a bright future in that country, which has 350 million web users. Google’s stock has dropped because of the shoving match with the Chinese government.
Story here: “Google Faces Fallout as China Reacts to Site Shift”
Is there a risk for China’s government?
Some have said that Google’s move to stop the censorship puts the authorities in China in a difficult spot. The government would be reluctant to anger Google users in China who are usually highly educated and who do complain, the Times said.
The paper quoted Bill Bishop, a Beijing Internet entrepreneur who writes the tech blog Digicha, “The Chinese are very serious about pushing their soft-power agenda, Google just put a big hole in that sales pitch, and I think they know that.”
In an analysis piece in the times, Michael Wines wrote:
“But China also does not acknowledge to its own people that it censors the Internet to exclude a wide range of political and social topics that its leaders believe could lead to instability. It does not release information on the number of censors it employs or the technology it uses for the world’s most sophisticated Internet firewall. Its 350 million Internet users, many with fast broadband connections, are assured they have the same effectively limitless access to information and communications that the rest of the world enjoys.”
Will forcing Google out stop innovation in China?
Wines and the reporters in Shanghai Beijing who contributed to the analysis also wrote:
“The cost, at least with some influential sectors of its own society, could be steep. In the technology sector, Google is viewed as an innovator that has spurred rapid development of the Chinese Web. Its departure will leave some Chinese companies with greater influence, but could also stifle competition, some fear.
“‘Google is good at innovation, and when it leaves, the rest of the companies in China will lack motivation. Without its countervailing power, the industry won’t be as healthy,’ said Zhang Yunquan, a professor at the Institute of Software at the Chinese Academy of Sciences.
“Fang Xingdong, chief executive of Chinalabs.com, said the vast majority of Chinese Internet companies invested little in research and ‘simply copy each other’s technology.’ With Google’s departure, their profits may rise, but China’s Web space will begin to stagnate, he predicted.”
Story here. “Stance by China to Limit Google Is Risk by Beijing”
What nastiness is in it for the rest of us?
It’s a clash of the Titans and there could be continuing fallout for everyone else. Although the wrestling match with Google didn’t start the hacking and intellectual property theft via Internet out of China, it could focus the attentions of nationalistic and quite independent Chinese hackers. We won’t even go into the issue of possible government- and military-sponsored hacks.
Enterprises should redouble user education about phishing and everybody better keep operating systems and anti-malware updated.
And, if you live outside China – enjoy the luxury of an uncensored web.
Tom Kelchner
Update 03/25: