Robotic software programs, called ‘bots or agents, automate actions that are typically performed by real people. ‘Bots can be used for good purposes or good – there are ‘bot programs that play games over the Internet, for example, and ‘bots that collect information for search engines, like the GoogleBot. Programmers have used ‘bots on eBay to automatically search the site for bargains. ‘Bots are common on the Internet Relay Chat (IRC) network, where they can moderate a channel by “listening” for profanity or other undesirable conversation and removing violators from the discussion. So-called ChatBots can carry on conversations over Instant Messaging programs.
Unfortunately, ‘bots have gotten a bad reputation because attackers can use them for malicious purposes, such as coordinating a distributed denial of service (DDoS) attack to overwhelm and crash a company’s network. The first ‘bot attacks were against IRC servers but the practice soon spread way beyond IRC. Other uses of ‘bots include:
- ‘Bots have been used to commit “click fraud,” where the ‘bot pretends to be a Web user clicking on an ad, to generate a high number of pay-per-click fees paid by the advertiser to the site owner.
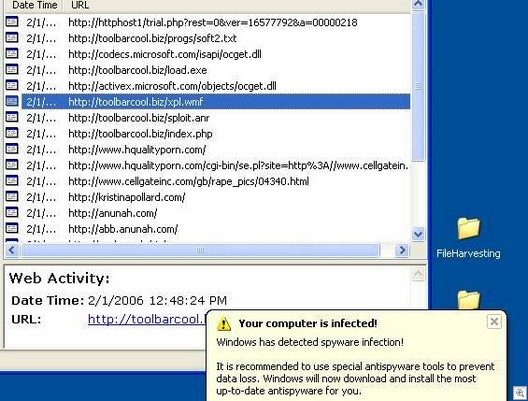
- ‘Bots can collect information such as the passwords, credit card numbers and other confidential information that users type into Web forms for the purpose of identity theft.
- Another malevolent use of ‘bots is to relay spam, to hide the identity of the sender.
- ‘Bots can sniff network packets to read the data inside, and use keyloggers to capture everything a user types.
- ‘Bots can spread new ‘bots, thus propagating themselves through HTTP, FTP or email.
- ‘Bots can manipulate online polls and ratings, so that the ‘bot can greatly increase – or decrease – the apparent popularity of a book on Amazon, an article on a Web site, or a candidate in a political poll. Each ‘bot has a different IP address, so the votes seem to be coming from different, legitimate voters.
What happens when lots of ‘bots get together? Somewhat like an unruly mob, they can do more harm working in conjunction with each other than individual ‘bots can do. “BotMasters” are people who run robot networks called BotNets, using worms, Trojans and backdoors to install the ‘bot software on the systems of unsuspecting users. Then each user’s computer becomes a part of the BotNet, which is controlled by the BotMaster.
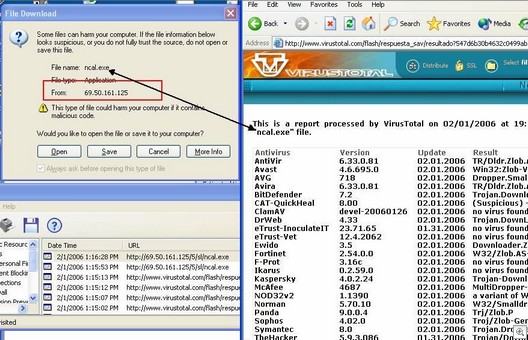
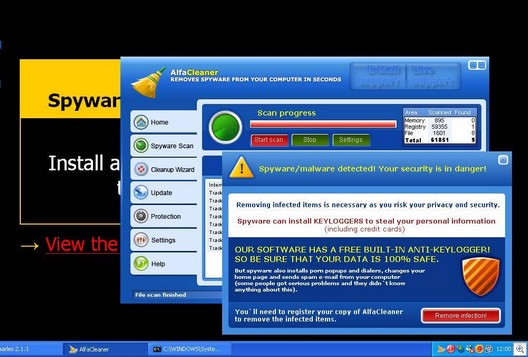
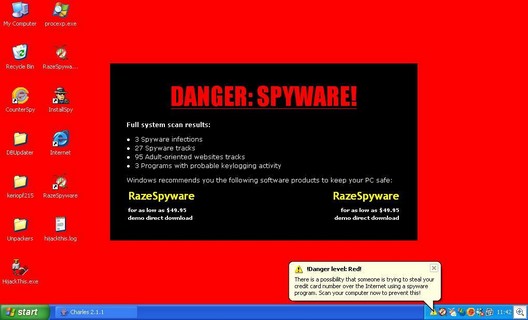
The ‘bot software is hidden from the user, who has no idea his/her computer is being used to commit attacks, intrusions and theft of data, or to distribute spam, spyware, and viruses. Because the systems are under the control of a remote entity, they’re often called “zombies.” For a quick overview of how BotNets work, watch the video called “About BotNets” linked here. (Quicktime).
Last October, Dutch police shut down a BotNet that included more than 100,000 computers and arrested its perpetrators. The BotMasters were using the zombie computers to attack networks and hack into bank accounts and PayPal and eBay accounts. You can read more about it here.
The incidence of BotNets (or at least, those that were discovered) started increasing enormously in 2004 and continues to rise. According to Symantec’s Global Internet Threat Report in 2005, there was a 140% increase in the number of active ‘bots observed per day over the previous reporting period.
BotNets have become big business. BotMasters will rent the use of their BotNets for 10 to 25 cents per machine, so that those without the technical savvy to set up their own BotNets can still have the use of one to launch attacks, distribute spam, commit identity theft, or whatever other nefarious activities they wish. Some common ‘bot programs include:
- Agobot/Phatbot/Forbot (there are more than 500 known versions)
- SDBot/RBot/UrBot (published under the Gnu Public License)
- GT-Bots (IRC script-based ‘bots)
- Q8 Bot (for UNIX/Linux systems)
- Perl bots (written in Perl scripting language, also used on UNIX systems)
How do you protect your computer from becoming a member of a BotNet? The same way you secure it against other threats: Update your system to the latest security patches religiously (and SP 2 really helps); and install good firewall, antivirus and anti-spyware software. Tight on cash? Read our Security on the Cheap writeup here.
Let us know your experiences with ‘bots. Are you worried about the BotNet threat? Have you ever discovered ‘bot software on your system? What measures do you take to protect against becoming an unwitting member of a ‘bot army? Tell us what you think about ‘bots.
Deb Shinder