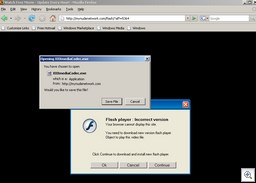
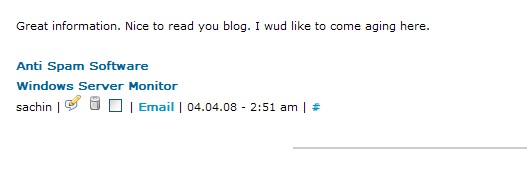
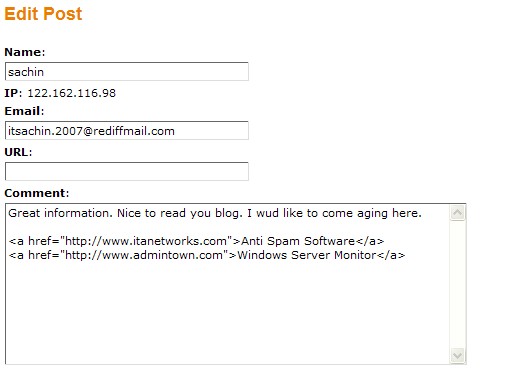
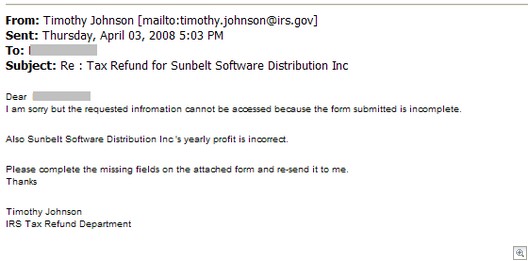
Mildly off-topic, but CNET has an article about online retailer Zappos getting into electronics and other products. It’s worth a quick read if you buy a lot online.
I do a lot of shopping online, and bar none, Zappos is absolutely, hands-down, the best internet retailer I’ve ever dealt with. The customer service is just flat-out amazing, and you really get the idea when you’re dealing with them that the CEO’s customer-oriented approach has filtered through the whole organization. Plus, they have a blog which is just as odd as mine. And the CEO, like me, is accessible by email and actually answers it.
Now that they’re getting into other areas, I’ll plan on looking to them to buy other things.
Alex Eckelberry