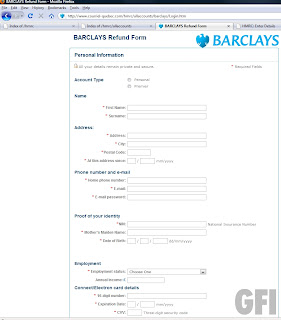
Thanks to thenext50k for sending this over.
From: “Paul Anderson”
Date: Thu, 17 Mar 2011 20:33:07 +0100
Subject: Urgent response as regards the Japan Earthquake, Tsunami
Private and Confidential
Firstly, I apologize for sending you this sensitive information via e-mail instead of a Certified mail/Post-mail. This is due to the urgency and importance of the information. This project is based on trust, confidentiality and sincerity of purpose in order to have an acceptable meeting of the minds. I am the account manager of Unity Bank Nigeria, West Africa with branches all over the world and almost in all parts of Asia. My name is Paul Anderson and I work both as an auditor and a consultant with the bank.
11 years ago, an expatriate, a Japanese from Tokyo Japan whom was also a client of the bank I work for successfully invested the sum of $26.2M USD with the bank I work for. On routine audit check I discovered that this investment account have remained dormant for some years. An investigation regarding the status of the account was carried out. However, during the course of the investigation, it was then revealed that the account holder (Expatriate and Investor) died in the Tsunami Earthquake disaster which took place on March 16, 2011 while on vacation. It was also discovered that the late client died intestate (died without a valid will) as he has no relation that knows about this deposit. Until his sudden demise, He was not married and was 44 years old.
NOW THE CRUX OF THIS E-LETTER is that banking regulation/legislation in Nigeria, demand that I notify the fiscal authorities after a statutory time period when dormant accounts of this type are called in by the monetary regulatory bodies. If no beneficiary to the investment account is presented as the late client’s next of kin within the next 14 official working days so that He or She can be paid the outstanding USD 26.2 Million dollars, the funds/payment will be diverted to the government coffers account as unclaimed bill and it may surprise you to know that funds of this nature are usually embezzled and diverted by corrupt government officials into their pockets to be used for their own selfish gains The above set of facts underscores my reason of writing and making this proposal.
Since we have been unsuccessful in locating any of his relatives, I decided to contact you for a deal so that we can work together as a team to remit the money to your account as my client next of kin since I do not want to sit and watch my client’s hard earned entitlement to go astray, it will be easy for us to achieve because you are of the same name like him. Although I know that a transaction of this magnitude might make anyone apprehensive but I would like to assure you that I am proposing this project to you with the best of intentions.
All I require from you is your honest co-operation to enable us seal this deal through. I guarantee that this transaction will be executed under a Legitimate banking arrangement that will protect you from any breach of law. Upon successful conclusion of this project, you will be compensated with 40% of the total fund, while 60% will be for me.
If you are interested to work with me in this deal of mutual benefit, kindly reply strictly to my personal Email: stating your full names, telephone, fax and mobile numbers for effective communication and oral clarification on how to proceed next, postal address, occupation and position held, scanned photocopy of your identification in the form of international passport or driver’s license or other to enable us prepare all necessary bank papers to effect the quick release of the funds into your nominated bank account.
Sincerely yours,
Paul Anderson.
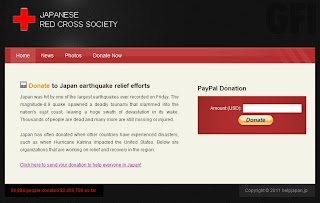
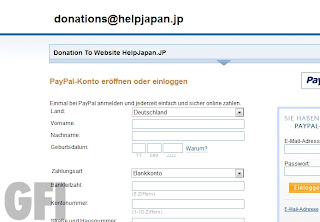
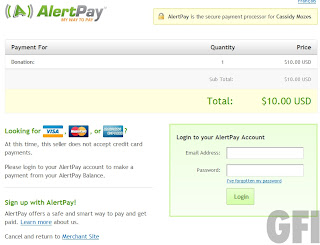
I’m struggling to think if there’s any kind of scam left untouched where the Japan quake / Tsunami is concerned.
Christopher Boyd