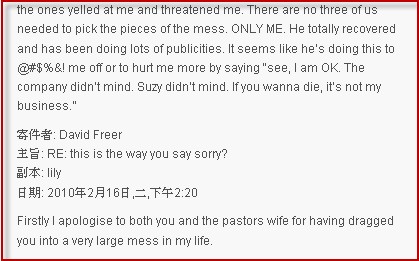
Psychology today: “… money-grabbing pseudoscience.”
Parts of this country seriously need more science education.
There are stories running today about “I-dosing” — Kids inducing a state of ecstasy by listening to special MP3s.
The sources for the story include The Oklahoma Bureau of Narcotics and Dangerous Drugs and either Kansas or Oklahoma News 9 and either Kansas or Oklahoma Mustang Public School District (some people are just scraping news stories and aren’t checking sources.)
Wired is carrying the story “Report: Teens Using Digital Drugs to Get High”
To their credit, they categorize it as “ridiculous.”

The Psychology Today blog “You 2.0” by Ron Doy has some interesting insight:
“But really, Idozer (or I-doser as it is also known) is extremely old drug in a new package. And breathe easy my fellow parents—because it’s not really a drug—it’s binaural beat therapy.
“In 1839, Heinrich Wilhelm Dove discovered that two constant tones, played at slightly different frequencies in each ear, cause the listener to perceive the sound of a fast-paced beat. Calling this phenomenon ‘binaural beats,’ Dove helped launch two centuries of legitimate research and, as is almost always followed by exciting empirical study, money-grabbing pseudoscience.
“First, the facts: Binaural beat therapy has been used in clinical settings to research hearing and sleep cycles, to induce various brain wave states, and treat anxiety.
“But there are more controversial (dare I say dubious?) claims associated with binaural beats: Increased dopamine and beta-endorphin production, faster learning rates, improved sleep cycles, and yes, if you dig around less scientific communities like, oh, MySpace, you’ll find kids telling each other that ‘dude, those beats get you like totally high.’”
Blog here.
And some reports from ACTUAL USERS!!!
“Well. I certainly wouldn’t call my self “high” at the moment, but it certainly does something to say the least. Maybe the onset of a migraine.. fun. Oh, and now my hearing is all f****ed.”
— “Largely a droning noise”

— “searched for gates of hades n youtube…turned it off after about 5 seconds.”
— “Yah. It feels kind of like I took a hit off of a roach that had been sitting in someone’s ashtray for a half a year. Not high, just kind of sick and headachey. Lame.”
— “ya, I tried it to. Kind of disorienting hearing 2 different things going on in either ear, and when it got intense enough did distort my vision, but…I definitely wouldn’t call it ‘high’ :”
Thanks Wendy (God! Where do you find this stuff!)
Tom Kelchner