“Faceparty is a UK based social networking site allowing users to create online profiles and interact with each other using forums and messaging facilities similar to email” – Wikipedia
Faceparty does things a little differently to other social networking sites, however. Unlike most places where you register a username and password then start telling people how your farm is doing, to join Faceparty you need to send a text message to the tune of £25 / $38(!) and then enter your one time use password onto this page (warning: quite a few swearwords, because the site is indeed down with the kids).
As you can imagine, obtaining these passwords has become a bit of an obsession for some people. Scroll down on that link, and you’ll see the following:
“facepartypassword(dot)com, got mine free today woohoo!” posted by “Chelsea Davies”, who somewhat suspiciously lists their own URL as the very same domain.
Shall we take a look?

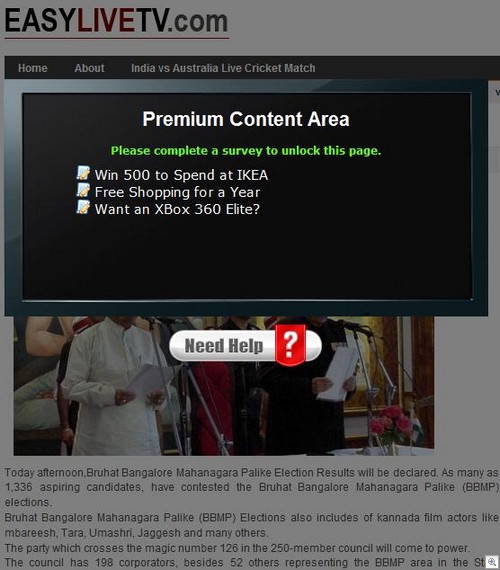
Yes, despite the passwords costing £25, this random website will “create a profile 100% free” – and all you have to do is fill in the desired username, password and email address.
This is what you see next:

Yes, it all goes wrong very quickly. You have to click your way through no less than five advert banners, each of which will take you to websites sporting people who seem to have forgotten to put some clothes on. Remember – “If you don’t click all the banners, you WILL NOT be sent the password!”
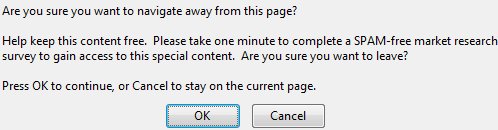
I don’t know about you, but I’m not entirely convinced here. Once you hit the Next button (just out of shot), this appears:
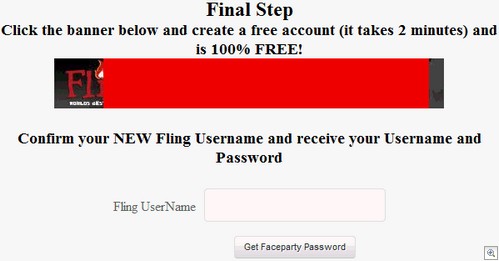
As you can see, they really want you to keep clicking that Fling banner advert. And wait, only a page earlier they were saying you didn’t have to join – now you do?
Someone is probably raking in a fortune in affiliate signups / clickthroughs here. Can you guess what happens when you hit the “Get Faceparty Password” button?
Sure you can. It doesn’t involve passwords, I can tell you that much – instead, you’re redirected to a specific profile on a site called Adultwork(dot)com, which advertises the services of more people who like to take their clothes off.
A few days later, and (amazingly enough) the email address I used to jump through hoops on the Facepartypassword(dot)com site still hasn’t had a password sent through to it. When I revisited today a new page was appearing at the start of the “signup process”, too:
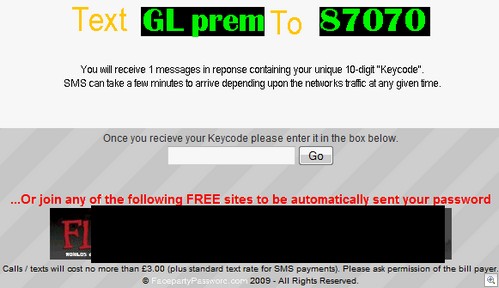
Yes, a £3.00 / $4.60 text message will get you your “Keycode”, or you can join Fling.
Again.
The thing that particularly caught my eye was that for a split second when visiting the site, a page will flash up before you’re taken to the first form to fill in. If we get all technical (and by technical, I mean reload the page then hit the Stop button on your browser as fast as you can) you’ll see this graphic, with two links at the bottom of the page that will send email to the site owners:

“Share the password”? “Sell your profile”?
Oh boy.
Christopher Boyd