We’ve got a building going up on SL (it’s actually a replica of our actual building here in Clearwater). Type in “Sunbelt” in SL to find our island. It’s still being built, be ready in a few weeks.

Alex Eckelberry
The Legacy Sunbelt Software Blog
The Great Years: 2004-2010
We’ve got a building going up on SL (it’s actually a replica of our actual building here in Clearwater). Type in “Sunbelt” in SL to find our island. It’s still being built, be ready in a few weeks.

Alex Eckelberry
Remember Steve Jobs’ quote about Apple as “musicians and poets and artists and zoologists and historians who also happened to be the best computer scientists in the world”? That’s his old quote about the Macintosh team, and it’s one of my favorites (I admit to being a bit nostalgic about the old days, when the software business was not a fashionable post-MBA career, but often a world littered with freaks, oddballs and some of the brightest minds you could find).
You can see the difference between the two CEOs of Apple and Microsoft. Here, Ballmer laughs about the iPhone’s high price in this video (via):
Jobs, on the other hand, practically conjures up magical genies and phantasmagoric images with his presentation of the iPhone. Incredible salesmanship? Yes. But the entire presentation is soaked with Jobs’ extraordinary vision.
Say what you want, but the difference between the two companies can be quite striking. No, I’m not bashing Microsoft. My only point is the difference in style (and it’s worth noting that despite all the grumblings about Microsoft, they have some of the best engineers and developers in the business).
I won’t be going out to replace my PC anytime soon with a Mac. But that iPhone… boy, that is interesting
Alex Eckelberry
More information is coming out about the trial, and it’s clear that we have a miscarriage of justice here. I hope to write more today or over the weekend as to some of the new information (short on time right now).
However, Altnernet just posted an article which explains a lot more about this case. It’s generally accurate, based on the research I’ve been doing:
When lax cybersecurity meets anti-porn hysteria, an innocent computer infection can land you in jail. Just ask Julie Amero, a 40-year old substitute teacher who maintains she’s a victim of a malicious software infestation that caused her computer to spawn porn uncontrollably.
Alternet also spoke to the defense’s forensic expert, Herb Horner. I’ve spoken with Herb as well, and he’s a good guy and is absolutely devastated by what happened. He’s quoted in the article:
“This whole trial was so unfair,” Horner said. “When Julie was convicted, I went home that night. I was eating dinner, and I started crying. I just cried my eyes out. This was a total travesty of justice.”
He’s right.
Alternet link here.
Alex Eckelberry
Consumer Reports pulls car seat report due to flawed methodology.
NHTSA that raised questions about whether the tests conducted by the non-profit group accurately simulated the conditions they were supposed to.
“Our initial review of the Consumer Reports testing procedures showed a significant error in the manner in which it conducted and reported on its side-impact tests,” said NHTSA Administrator Nicole Nason in a statement posted on the agency’s Website.
If you’ll recall, last year a number of people in the industry had serious concerns about Consumer Reports’ testing methodology for spyware and viruses. Their antispyware testing was, bluntly, laughable.
So, how many consumers will continue to be misled by CR’s testing methodology? I know I get comment storms from CR supporters, but we know of so many flawed tests — everything from hybrid cars, cat food, cameras and flipping Suzukis. I would postulate that the reason for their problems is that the organization fiercely believes in its independence, which means that they may not consult with industry experts who know more about how to test their own products than the testing organization itself. There is bias. There is also expertise. The two can be mutually exclusive.
Alex Eckelberry
I’m scheduled to be on the Craig Crossman radio show tonight, discussing the Julie Amero case.
8 pm PDT, 11 pm EDT.
Streaming link here. If the link doesn’t work (I’ve been having problems with it myself), try it off the main site.
Just recently, we’ve seen a couple of cases where investigators and prosecutors have gone after serious criminal convictions against people with porn on their systems — Julie Amero’s case and the recent case involving a teenager. In both cases, the defendants had systems that were infected with spyware. And in both cases, the prosecuting parties did not appear to fully comprehend the problem.
Yesterday, Francesco in our spyware research team took a video which clearly shows what can happen in a spyware infestation that results in porn popups. In this case, the machine was infected by the HotSnow trojan (a nasty new rootkit-based trojan) while visiting an innocent site. The infestation, which appears related to a KlickVip affiliate, infected the machine through the use of a now-patched exploit (MDAC).
Notice that the infection site was a relatively innocuous gaming site. Note the immediate porn popups (and this was very hardcore stuff which we had to heavily pixelize) as well as the fact that the images from the popups are then stored on the user’s PC, which Francesco shows by going to the local temporary internet files directory.
To an untrained investigator, the popups will appear to be sites that have been visited, rather than popups. And images from the popups are stored locally on a PC. (Of course, there’s also the even worse situation where one could have a trojan turning your system into an FTP server serving porn.)
You can see the video here.
The old adage “where there’s smoke, there’s fire”, isn’t necessarily applicable in these types of situations. It takes expert forensic investigation and a thorough knowledge of the problem before one can come to the conclusion that a real crime has occurred, rather than popups from an innocent spyware infection or web browsing.
Alex Eckelberry
An email address on my personal domain has been spoofed and I’m getting a godzillion bounce messages sent to my home account. The address is not a real one, but since I’m the administrator on the account and it’s set to catch-all, I get all the joy.
The only thing to do in this case is to either a) kill the email address or b) put a rule in place and wait it out.
Irritating.
Alex Eckelberry
Vista Ultimate Extras unveiled
One of Microsoft’s stated benefits of buying the most expensive Ultimate edition of Windows Vista was that it would be able to run free “extras,” software applets that would be released later. But we were left to wonder what those extras might be. At CES last week, we got a glimpse of some Vista extras that are scheduled to be released in conjunction with Vista’s release to the general public at the end of this month. They range from a Hold ‘Em poker game to a secure online key backup program for BitLocker.
One of the most interesting was called DreamScene. It will let you set an .MPEG or .WMV video as your desktop wallpaper, just as you can choose a picture now. To use it, you’ll need an Aero-capable video card.
For more about these three Extras, click here.
More about Choosing Passwords
Last week, we talked about the difficulty of creating passwords that are both secure and memorable. In this article, Joe Wilcox reveals password weaknesses of many sites and programs, and points toward a link that features a primer on how to choose passwords and secure Adobe PDF files, much of which is applicable to password selection in general.
You can also install the tools from the command line, by typing the following at the command prompt: msiexec /I x:supporttoolssuptools.msi. For a complete installation, add the addlocal=all switch.
Dual booting 32 and 64 bit Windows.
Technically, there’s no problem with dual booting the 32 and 64 bit versions of Windows Vista (or Windows XP, for that matter) on a 64-bit capable system. You should install each OS in its own partition, though. A problem with many OEM systems is that the vendors ship them with one huge partition. There are several ways to solve that problem. Perhaps the easiest, if you have an extra drive bay, is to buy a second physical drive and install it. That will give you more space (and you’ll need plenty of space with two instances of Vista) and a clean new partition on which to install the second instance of the OS. Other alternatives include reformatting your existing drive and repartitioning it (this may be the best if the computer currently runs XP and you want to start over with a clean installation of Vista) or using a third party utility such as the latest version of Partition Magic to resize your existing partition and create a new one.
However, legally there’s another issue: the End User License Agreement for the retail versions of Vista, states in section 2 (a) and (c): “You may install one copy of the software on the licensed device” and “The software may include more than one version, such as 32-bit and 64-bit. You may use only one version at a time.”
Direct link to PDF here.
Although one could argue that you’ll only be using one of the versions “at a time,” I think Microsoft’s interpretation will be that you need to buy two licenses. And while we’re on the subject of Vista licensing, readers should also note that Vista Home editions (Basic and Premium) cannot legally be used as guest operating systems in virtualization programs such as Virtual PC or VMWare. You can install Business or Ultimate edition as a guest OS.
User logon request is rejected without error message
If a restricted user with no password attempts to log onto Windows XP from the Welcome screen, and the logon request is rejected but you don’t get any kind of error message, it may be because the security log is full. There’s a hotfix available to fix the problem, but you have to call Product Support Services to get it. For more information, see KB article 313322.
Network Magic makes getting connected easier
At first glance, you might wonder why you’d need a third party product to set up your home network, since that’s all built into Windows. But if you have a network that’s a little complex or out of the ordinary, you may have endured hours of frustration, trying to get networking to work for you. In that case, a program that eases your way might be just the ticket. It can get especially tricky if you’re trying to connect computers running different versions of Windows. Network Magic can also provide some of the networking features that are in Windows Vista, like the Network Map, even if your network is running just XP computers. Check it out here.
You can also get a free scan of your network that will perform various security and performance tests and detect the devices connected to your network (you’ll have to download an ActiveX control) here.
Deb Shinder, Microsoft MVP
Tom and I spent last week at the Consumer Electronics Show (CES) in Las Vegas and as always, it was overwhelming. Crowds at the Microsoft booth were especially large; you you felt as if you were taking your life into your own hands to fight your way to the front of the Vista Home Server, Ultra Mobile PC and Xbox 360 displays. If you’d like to see photos of some of the tech toys we saw there, check out my blog.
TVs were, no pun intended, on display everywhere. They ranged from tiny handheld models to movie theater-like giant screens, and picture quality on some models was amazing. Bigger may be better, but it doesn’t come cheap. Sony’s 70 inch 1080p LCD goes for $33,000.
Sharp unveiled the world’s largest full HD LCD with a breath-taking screen that measures 108 inches, but they’re not telling the price (it won’t be available until later this year).
But why buy just a TV when you can get a device that combines multiple functions? It seems as if the main theme this year was “convergence” – we heard the term over and over and saw numerous examples of converged technologies. TVs converged with computers, computers converged with phones, IP phones converged with PSTN phones, retro designs converged with futuristic functionality. Everywhere you looked, something was converging with something else.
This rush to combine several devices or functionalities into one is a natural outgrowth of our electronics-dominated world. How many of you have three or four or even more remote controls sitting on your coffee table? There’s one for the TV, one for the DVD player, one for the sound system, maybe one for the Media Center PC … well, you get the idea. A universal remote that can control all of those components is a mighty attractive idea, but I can go you one even better; my Pocket PC, which is also a cell phone, includes remote control software that I can use for my home theater equipment. In fact, there are a number of such programs for the PPC.
Speaking of remote controls, some of the coolest things we saw at the show were the various models of SideShow remotes. These are remote controls for Windows Vista Media Center that have a tiny LCD screen with which you control things like music playback without even turning on the TV or monitor. Link.
Convergence of computer and cell phone is something that many of us want today, but there’s an inherent dilemma: we want our cell phones small, but we want our computers to be capable of full desktop functionality. How do you accomplish both? All of today’s solutions are compromises, but we’re seeing more and better efforts to provide both of these. My Samsung i730 PPC phone does pretty much what I want, but it’s a bit bulky and battery life leaves a lot to be desired. At CES, we got a look at the next generation: the i760. It’s slightly sleeker and the model we saw there (as opposed to those we’d seen previously on the Web) has a side-slide keyboard.
The Samsung that was getting the most hype, though, was the Blackjack. There was even a huge ad for it on the front of the Las Vegas Convention Center. It’s actually a bit longer and wider than the i730, but significantly thinner. However, I don’t like that its keyboard is “out in the open,” rather than a slider.
Personally, I’d prefer to do away with the physical keyboard altogether and make the device thinner. I always use the on-screen keyboard anyway. Now Apple, with their just-announced iPhone (MacWorld’s attempt to steal the thunder from CES), has done just that. In fact, the Apple phone has many features I like, including a big screen and the elimination of a bunch of buttons on the front. I was excited when I heard that it runs OS X – but less so when I learned that it won’t allow you to install third party software, doesn’t have a memory expansion slot, and won’t support Exchange or Office. Not quite the level of computer/phone convergence I’d been hoping for. But hey, LG has a phone that’s similar in design to the iPhone (and in fact, came out before the iPhone was unveiled). Don’t know much about it yet, but it’s got my hopes up again. You can see it here.
One of the most interesting converged devices we saw was Samsung’s new P9000 “Communicator.” When you first get a look at it, you’re not sure exactly what it is. Its foldout keyboard “wings” remind me of a Lamborghini (but I’m hoping it’ll be a lot less expensive).
It turns out it’s a full fledged Windows XP computer with a 30 GB hard disk and a 5 inch screen but, unlike the Sony U series and various Ultra Mobile PCs, it’s also a cell phone. It works with CDMA and EVDO networks such as Verizon’s, but will also connect to WiMAX broadband networks. I figure it’ll either be a great success or a big flop. Since it was behind a glass case at CES and I wasn’t able to touch or hold it, I haven’t yet decided whether it’s the perfect size compromise for a computer/phone device, or whether it’s too big to work well as a phone and too small to work well as a computer.
The convergence trend continued as we encountered “smart” watches, “smart” coffeepots and other common household devices with embedded computers. This is obviously what the future holds, but which ones will catch on is anybody’s guess. I still remember the Samsung Internet-enabled HomePAD refrigerator that came out back in 2003.
Everyone ooh’ed and ahhh’ed at it in the stores, but I don’t know of anyone who actually bought one. Only a really dedicated gadgeteer would be willing to shell out eight grand for a fridge just because it has a monitor in the door.
Which brings us, in a round-about sort of way, to the real question of today’s editorial: just how far can/should convergence go? Combining devices certainly offers certain conveniences – who wants to carry around separate cell phone, PDA, and MP3 player if you can get it all in one compact package? But, as those who have owned printer/copier/fax machines and other combo devices know, there’s also a downside. What happens if one part of your multi-function device dies before the other(s)? Now do you have to throw away a perfectly good MP3 player because the phone quit working?
And some devices seem to take convergence to the point of being ridiculous. Do I really want a coffee cup that can connect to the Internet? A pair of sunglasses that plays video games? I haven’t even yet accepted the idea of having a camera built into my phone; watching all those folks in Vegas taking pictures with their cell phones was a little disorienting. I guess it’s convenient, but there are just too many places where cameras aren’t allowed, and I don’t want to have to give up my phone every time I enter one of them. I’ll stick with my dedicated Nikon for now.
Tell us what you think. Do you like having all your devices combined, or do you prefer separate, dedicated devices, at least for some functions? What (if anything) would you like your cell phone to be able to do that it doesn’t now? Are you a fan of unified communications, where you can receive and send your phone calls, faxes, email and instant messages from a single interface or device? What’s the most ridiculous “combo” device you’ve seen or heard of?
Deb Shinder, Microsoft MVP
George Danziger, a retired school IT administrator, comes to the defense of Julie Amero, the hapless substitute teacher who is facing 40 years in prison due to a porn spyware infection on a classroom computer.
Julie Amero is as much a victim as the students of what happened in that
classroom. The actual perpetrators were the pornographers who generated the
porn, the Web site operators and all who facilitated delivery of the porn —
including the school administration, which failed to provide a safe workplace,
staff training and functioning content filters.
Link here.
Good for you, George.
Alex Eckelberry
Last week, a few of us got a bit upset at Preston Gralla at ComputerWorld, who blogged that Julie Amero had been rightfully convicted of surfing porn (this is the middle-aged substitute teacher who had a porn-spewing spyware infestation on her computer, and is looking at 40 years in prison).
He wrote me a gracious email this evening to tell me that he wrote a follow-up to his last post, where he states that if the machine was, in fact, infected with spyware, than it is a miscarriage of justice.
…I haven’t personally seen the teacher’s PC. But if in fact it was infested with spyware, as people say, and if the school system let the site filtering lapse, then what happened is a miscarriage of justice. And if that’s the case, I clearly wrote my blog before knowing the facts, and was flat-out wrong.
It takes a quite a man to make a statement like that. Preston: I salute you.
Folks — feel free to follow-up on his site with a comment. His blog post is here.
And just to recap the facts of the case as we know it:
Not that it’s probably legally relevant, but the activities of the court may have cause for some suspicion. One source reports that the Trial Judge, Hillary Strackbein, “was seen falling asleep during proceedings and made comments to the jury that she wanted the case over by the end of the week. It was also reported that Judge Strackbein attempted to pressure the defense into an unwanted plea deal, in place of a trial. The defense attorney for Amero, moved for a mistrial shortly before closing arguments Friday, based on reports that jurors had discussed the case at a local restaurant.” (I believe that the judge questioned the jurors subsequently and they denied having discussed the case.)

Our email security product, Sunbelt Messaging Ninja, has won the Silver award for TechTargets list of Products of the Year.
The Sunbelt Messaging Ninja Version 2.0 won the Silver Award in SearchExchange.com’s Products of the Year 2006 Exchange Server Security category. Judges gave it high scores for ease of use, value and performance — and a perfect score for functionality because of what they called its plug-in architecture and out-of-the-box modules.
“Organizations looking for an all-inclusive antivirus, antispam and anti-phishing solution for Exchange Server at an affordable price will benefit from Sunbelt Messaging Ninja Version 2.0,” according to one judge.
A unique feature of Sunbelt Software Inc.‘s Ninja product is its proprietary attachment filtering technology, which offers advanced directional and source-level controls that block attachments no matter what the file is called or renamed. Signature and heuristics-based filtering ensure additional antivirus protection against unknown or zero-day threats.
Also, because it’s designed as a Microsoft Management Console snap-in, Sunbelt Messaging Ninja Version 2.0 is easy to set up and you can deploy it quickly with minimum configuration required.
Damn straight.
TechTarget PR link here. Award link here.
Alex Eckelberry
Our folks in spyware research infected two machines with spam bots (the spam bots are only sending to our internal research network — all traffic to port 25 is redirected to our honeypot).
By infecting two machines with two different known spam Trojans (Trojan-Proxy.Win32.Lager.gen and FiveSec.Spam.Agent.vx), we were able to capture over 6,000 image spam messages in a period of only 35 minutes (the spam bots were running at different times). Incidentally, these trojans are coming through Vxgames installs (nasty malware distributors).
So, with our bandwidth, these bots combined are capable of sending over 12,000 messages an hour – a little over a quarter million messages a day. At one time just one of the machines was pushing one megabit per second of spam email at the test server.
However, in real life, the real number would be lower, probably 60,000 to 80,000 messages per day (we’re dealing with fast DNS servers and gobs of bandwidth here, so our tests will always show higher rates than real-world). Still, that’s an incredible number for one machine.
A few different samples of stock image spam picked up Friday in our “SpamTrap”, all promoting a stock for Aerofoam Metals (AFML):
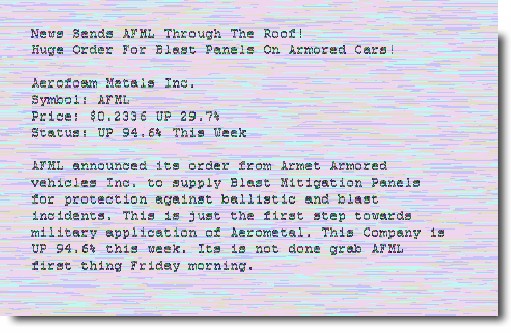
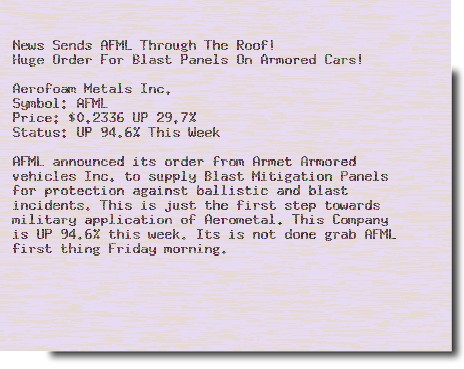
And here is that stock on Yahoo finance:
And that’s why you see so much spam.
Alex Eckelberry
(Credit to Sunbelt researchers Adam Thomas, Tom Robinson and Nick Suan)
A prominent journalist told me at CES, “There are only two people who will use Vista: Those forced to when they buy a new PC, and those who will upgrade in 5 years”.
Now a blogger weighs in on Vista with guns blazing, even associating poor Humphrey, the three-legged camel:
Opinion. It sucks. It’s a complete mess; a dog’s breakfast. It’s bug-riddled; it contains legacy features that hark back to Windows 3.1, and, worst of all, it can’t be trusted with your valuable data. The user interface only looks slick; underneath it’s a slapped-together hotchpotch of brain-dead, dysfunctional and downright buggy features. Windows Vista was surely designed and built by the same well-meaning but thoroughly misguided committee of morons who were responsible for the three-legged Bactrian camel named Humphrey.
To read more, click here.
I’ve certainly expressed some doubts as well, but I wouldn’t characterize it as that bad.
Forget Linux, which will dominate on the server, but not on mass market desktops (sorry, Linux people, I’m a huge Linux fan but this is the simple truth). Think Apple: Will 2007 be beginning of the tipping point for Apple? I played Job’s iPhone keynote address to my kids and they were enthralled. No one cared about Gates’ keynote. Apple has captured the minds and hearts of the youth generation, and their humorous but irritatingly arrogant TV ads notwithstanding, there are few reasons not to get a Mac these days. After all, we’re in the LoneyGirl15 generation now. It’s all about the web.
Alex Eckelberry
iPhone: I’m sick of people bashing the iPhone already. It’s a damned cool phone. I admit I have some pet peeves, like the fact that it runs on Cingular (I’m on T-Mobile) and the built-in battery. But darn it, Apple did an impressive job with this phone.
The death of BlueRay? A straw poll of the porn industry shows that the preferred format is HD-DVD. Regardless of your feeling about porn, refusing to service this market may very well be the death knell for the BlueRay format, despite Sony’s massive film library. The race is still too close to call, but Sony really needs to open up here.
Amazing children. On one side, I’m blown away by the artistry (it is a must see video). On the other, I’m a little unnerved at this video of children parading in North Korea (what happens if they screw up, are they sent for “re-education”, never to return?). Or, they just starve.
Alex Eckelberry
You’ll recall the case of Julie Amero, the hapless substitute teacher who has been convicted for a porn spyware infestation on a classroom computer and is now facing up to 40 years in prison (sentencing is on March 2).
The tech community has, for the most part, been quite supportive of Ms. Amero (some comment storms here and here). It’s deservedly become a cause celebre.
However, ComputerWorld blogger Preston Gralla feels quite differently. In a posting today, he crows that “justice prevails”:
Lawyers have come up with some novel defenses over the years, including the “Twinkie defense” in which a lawyer argued that defendant Dan White’s eating of Twinkies and drinking Coca-Cola proved that he was depressed, and so not responsible for his actions in murdering San Francisco Mayor George Moscone and Supervisor Harvey Milk in 1978. The defense was partially successful; White was convicted of voluntary manslaughter rather than murder.
Luckily, it seems as if the spyware-made-me-do-it defense doesn’t cut it in court. For once, justice prevails.
Link here.
Preston makes a clever twist, mixing an obvious abuse of the court system (the twinkie defense) with an arguably legitimate defense (spyware), an argument ignored by an apparently computer-illiterate court (and the defense lawyer admitted to me today that he also is computer illiterate). (Update: It turns out the Twinkie Defense itself is not real).
There is abuse in our justice system, with incessant victimization which attempt to remove responsibility from the perpetrator. However, we also suffer from a system of mores where armchair jurisprudence creates instant “conclusions” and damnation of the convicted, often based on emotional reaction, rather than a review of the evidence. Having personally witnessed first-hand a genuine miscarriage of justice, I tend to be a bit more cautious in my conclusions. As surprising as it may sound to some, not everyone indicted or convicted is guilty. Some are actually innocent.
In fact, this case shows that the evidence is not in favor of the “justice prevails” argument, but quite the opposite.
My response to Preston:
Justice? No, the evidence to hand actually points to a miscarriage of justice.
This case is so wrong on so many levels. Julie Amero is looking at 40 YEARS in prison. For a spyware infestation.
Every available piece of evidence known to the public indicates that that Ms. Amero is quite likely _innocent_ of the charges.
The defense contends this was a case of spyware on the school machine — a barrage of popups. And from what we know of the case, it certainly looks like it was (if you want to see what a porn spyware infestation actually looks like, Ben Edelman shows it here: http://www.benedelman.org/news/062206-1.html — it’s quite a real problem).
According to one article, “Computer expert W. Herbert Horner, who performed a forensic examination of the computer for the defense, said Amero may have been redirected to the sexually-oriented sites through a hairstyling site accessed from the computer. He said the site allowed spyware to be downloaded onto the computer which allowed the pop-ups.”
The detective in the investigation “admitted there was no search made for adware, which can generate pop-up advertisements”. It’s incredible that they never even _checked_ for spyware.
The court actions of the case were flawed as well. For example, one source reports that the Trial Judge, Hillary Strackbein, “was seen falling asleep during proceedings and made comments to the jury that she wanted the case over by the end of the week. It was also reported that Judge Strackbein attempted to pressure the defense into an unwanted plea deal, in place of a trial. The defense attorney for Amero, moved for a mistrial shortly before closing arguments Friday, based on reports that jurors had discussed the case at a local restaurant.”
Finally, note that the school didn’t even have active content filtering in place (not that it would have probably made a difference).
The fact that there were pornographic images on the computer means nothing, because whenever a popup launches, the images in the popup are stored on the computer. The fact that the logs indicated that she “visited” the sites also means nothing, since when the porn popups come through, they get logged as well.
The fact that the machine was never scanned for spyware by the investigating authorities is outrageous. In fact, this alone should have resulted in the case being dismissed, as the defense found a major spyware infection by their expert forensic evidence.
Was justice done here? A bad spyware infestation can splatter a machine full of porn popups and it’s a bit unnerving to think that a teacher could get hard prison time for something that was likely to have been completely innocent.
We need far more evidence than what is available to come to the conclusion that “justice was done”. In fact, all the available evidence shows quite the opposite — that this might just be a grave miscarriage of justice.
If you feel the same, post a comment on Preston’s blog.
And, if you’re wondering what a porno-spawning spyware infestation looks like, here’s some examples from Harvard researcher Ben Edelman:


I also should note that in a conversation with the defense attorney today, he did tell me that his computer experts were not able to provide all the evidence in court. For the appeals process, we have made our own experts available to the defense on a pro-bono basis for any analysis of the infected machine.
Alex Eckelberry
Another off-the-wall, stupid law passed by Internet luddites.
South Korea has now passed a law that requires people to use their real names.
The system will require Web users to identify themselves with their real names
when posting entries and commenting on others’ articles, the government said
yesterday.
Link here.
While I sometimes wish that the trolls and spammers who frequent my blog were required to give their real names, the chilling effect of such a idiotic law on civil liberties is unnerving.
Alex Eckelberry
(thank Franceso)
A senior Microsoft exec complains that “craplets” (those programs that OEMs pre-load on their systems) could screw up the Vista launch.
In a discussion Tuesday night at the Consumer Electronics Show in Las Vegas, the Microsoft official told CBC News Online, on condition of anonymity, that the world’s largest software maker is frustrated by legal shackles that prevent the company from restricting what kinds of software major computer makers install on new PCs.
Link here (via Dwight Silverman).
Clearly, he must have said this after reading my blog post on de-crapifying your PC.
Alex Eckelberry
Yesterday, I blogged about Julie Amero, the apparently hapless substitute teacher who found herself barraged with pornographic popups on the classroom computer and has just been convicted for this “offense”. She’s looking at 40 years in prison.
Now, we find that the local newspaper actually supports the conviction, only feeling that 40 years might be excessive.
They admit that this 40-year old woman she has no criminal record, but her conviction is just, as they “expect that this sordid experience will serve as a cautionary tale to every parent, teacher and school administrator in Eastern Connecticut.”
Help me understand this.
Alex Eckelberry
Office and OS Patches Coming This Week
This month’s Patch Tuesday falls on January 9th, and we’re expecting Microsoft to release eight security bulletins, four of which include patches for vulnerabilities in Microsoft Office. Three bulletins pertain to Windows and one is for Visual Studio. Remember that critical security fixes will be downloaded and installed automatically if you use Windows Update/Microsoft Update in the default setting, but if you don’t, be sure to check out these patches. More here
Money back for unused Windows licenses?
We haven’t tried this ourselves, but according to this article, if you buy a new computer from an OEM that comes with Windows, but you are going to install Linux or another operating system on it and not use Windows, you can get a refund for the Windows license from the hardware vendor. You cannot have accepted the Windows EULA. Read more here.
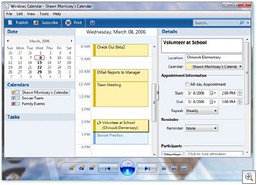 Windows Gets a Built in Calendar
Windows Gets a Built in Calendar
One brand new feature for Windows Vista is a built-in calendaring application, called – appropriately enough – Windows Calendar. It provides similar functionality to Outlook’s calendar feature, but it’s a separate application from Windows Mail. You’ll find it in the All Programs menu. As with Outlook, you can share your calendar with others, and you can create multiple calendars for different purposes and publish the calendars for others to subscribe to. Calendar items are color coded and there’s a search box for finding specific appointments and tasks. You can set up recurring events or add reminders so you’ll be notified prior to an appointment.
It’s a pretty full featured little application, and for those who don’t have Outlook, will make a valuable addition to the functionality of Windows. For more info and to see screenshots, click here.
How to save a search query
Much has been made about the cool new search features in Vista, but many folks aren’t taking advantage of all that XP has to offer in the search department. For instance, did you know you can save a search query for future use? Here’s how:
Search queries as saved as .FND files. By default, they’re saved in your My Documents folder. To use a saved query, just open My Documents or the location where you saved the .FND file and double click it. You can change the criteria before clicking Search if you need to.
Online Safety and Security Magazine
Microsoft is now publishing a Safety and Security online magazine that’s specially targeted at home users. You can download the inaugural edition on the Microsoft web site. Or you can subscribe to the free Microsoft Security for Home Computer Users monthly newsletter in either text or HTML format.
Do you want to change the default location for the My Documents folder?
If you want to the My Documents folder to a different location (for example, a different drive so that if you have to reinstall the OS, it will still be preserved), it’s a simple operation. The proper way to change the location of the My Documents folder is to change the target location, like this:
How to reset the nickname cache in Outlook
Outlook can automatically complete the names of recipients to whom you’ve previously sent mail, but if the cache gets corrupted, this feature may stop working. You can reset the cache by following the instructions in KB article 287623.
Extending the desktop while playing video may cause problems
If you’re running multiple monitors on XP and you try to extend the desktop to a secondary display while playing a video in Windows Media Player on the primary display, you may find that you lose the video portion, or that the video stops altogether and displays an error message when you try to restart it. This is caused by a problem with DirectDraw. For workarounds, see KB article 325771.
How to connect an Xbox 360 to an XP computer
If you’re one of many who received an Xbox 360 game console for Christmas, now all you need to do is connect it to your home network so you can view the photo and music files stored on other computers and the TV programs recorded by your Media Center PC (if applicable). For info on how to make the connection, see KB article 909536.
You get an error message when you try to add a printer
If you try to use the Add Printer wizard to add a local or network printer to your XP computer and you get an error message that says “Operation could not be completed. The print spooler service is not running,” this means the Spooler service has stopped working for some reason. You need to restart it, either via the graphical interface or the command line. For instructions on how to carry out both methods, see KB article 314876.
Deb Shinder, Microsoft MVP