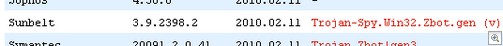
Security blogger Brian Krebs is reporting that some Windows XP users are reporting blue screen of death on reboot after installing Microsoft’s Tuesday patch KB977165 (MS010–15: “Vulnerabilities in Windows kernel could allow elevation of privilege.”)
“Turns out, a non-trivial number of XP users are reporting that their systems suffer from the dreaded Blue Screen of Death (BSoD) and fall into an interminable reboot loop after installing the latest batch of patches from Redmond,” he wrote.
Brian Krebs’ blog here.
Those trying to maintain Microsoft systems are caught in the cross-currents of the patching process: some patches might be buggy (think “delay”) but the dark side will be reverse engineering the patches as fast as they can (do it now.)
It almost seems like it would be a good idea for the users of Microsoft products to hold off about two days before installing the Patch Tuesday updates. That seems to be how long it takes for the word to get out – like this problem – that there are glitches in the updates.
The overwhelming number of Microsoft fixes are straightforward and urgently needed security measures. However, the massive complexity presented by the older flavors of the Windows operating system and service pack levels almost guarantees that there are going to be problems like this.
Possibly a good strategy would be phased updates especially for enterprise systems:
— Immediately install just the patches that fix vulnerabilities with in-the-wild exploits if you are running the vulnerable applications, modules, plug-ins, etc.
— Wait three days for all others
— Wait a week for non-critical (no reported exploits) updates to less-used flavors of Windows and less-used applications.
Meanwhile, have someone keep an eye on the security news sources to spot problems like this one.
Update:
Krebs’ blog carries some good, detailed advice for those whose machines have been disabled already by the glitch.
Computer World carried a story about the problem and noted:
“This was not the first time that a Microsoft update has incapacitated Windows PCs. Two years ago, a set of updates for Vista sent an unknown number of machines into an endless series of reboots. Similar problems stymied users who tried to upgrade to Windows XP Service Pack 3 (SP3) in May 2008, and others attempting to upgrade from Vista to Windows 7 last October.”
Update 02/12:
Today Softpedia carried a statement from Jerry Bryant, Microsoft’s senior security communications manager lead:
“We are aware that after installing the February security updates a limited number of users are experiencing issues restarting their computers. Our initial analysis suggests that the issue occurs after installing MS10-015 (KB977165). However, we have not confirmed that the issue is specific to MS10-015 or if it is an interoperability problem with another component or third-party software. Our teams are working to resolve this as quickly as possible. We also stopped offering this update through Windows Update as soon as we discovered the restart issues. However, those using enterprise deployment systems such as SMS or WSUS will still see and be able to deploy these packages.”
Update 02/15:
Researchers have theorized that the TDSS rootkit was responsible for the blue-screen-of-death problems after Windows XP users installed Microsoft’s patch MS010-15 last week.
Microsoft acknowledged the problem in a statement: “In our continuing investigation in to the restart issues related to MS10-015 that a limited number of customers are experiencing, we have determined that malware on the system can cause the behavior. We are not yet ruling out other potential causes at this time and are still investigating.”
News story here.
Update 02/16:
Our good friends at Symantec have posted more information on the problem and some instructions for recovering from the BSoD:
“Most of the time the driver chosen by Tidserv to be infected is “atapi.sys,” but that may vary depending on the hardware configuration. One of the very things the infected driver does when it is loaded by the operating system is to retrieve critical API addresses so that it can allocate memory to load the actual malicious code:
“These APIs are retrieved via hard-coded relative virtual addresses (RVAs) into the kernel module, which are calculated at the infection time. Microsoft recently released a kernel patch that addressed a non-related issue (MS10-015 / KB977165), which updates the kernel modules. They also released a blog about blue screen issues after applying this patch.
“What seems to have happened in Tidserv’s case is that after this update, the RVAs for the above mentioned APIs changed—therefore causing the infected drivers out there to call invalid addresses and, in turn, cause blue screens every time Windows boots up:
“Even worse, because the infected driver is critical for system boot-up, Windows will not boot in Safe Mode either. However, there is still hope for the users who get stuck in this infinite loop of BSoD, in the sense that they are not required to reinstall everything from scratch, but only the infected driver (from a known, clean source). And, here is an example for the most commonly infected system driver, atapi.sys:”
Symantec blog here.
Update 02/19:
SANS diary: MS10-015 may cause Windows XP to blue screen (but only if you have malware on it)
“Lucky for us the malware writers have addressed this issue and it shouldn’t happen again for those who are newly infected with this particular piece of malware. A shame really, as it was a convenient way in which to identify infected machines. If you did get the BSOD on your machine or on machines in your organisation, then you should consider the possibility that the machines are infected.”
Tom Kelchner