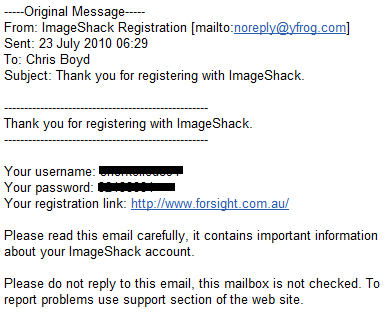
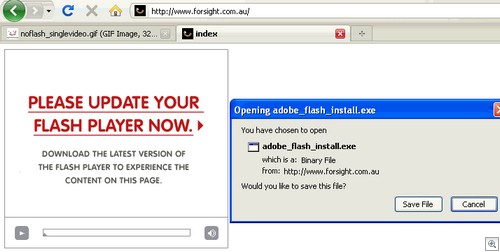
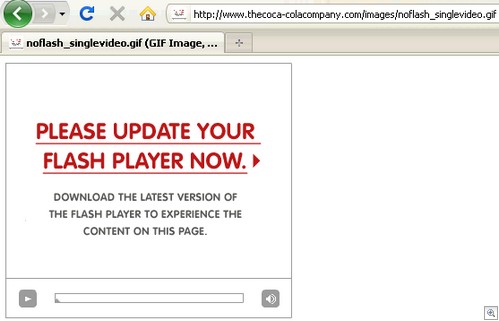
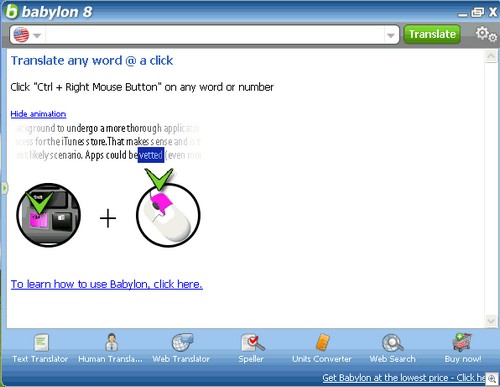
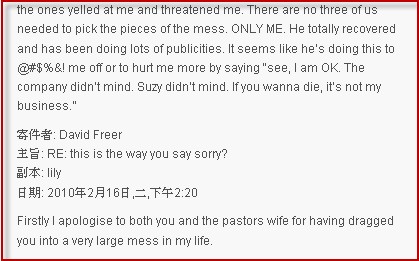
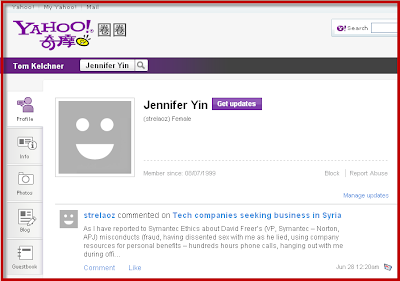
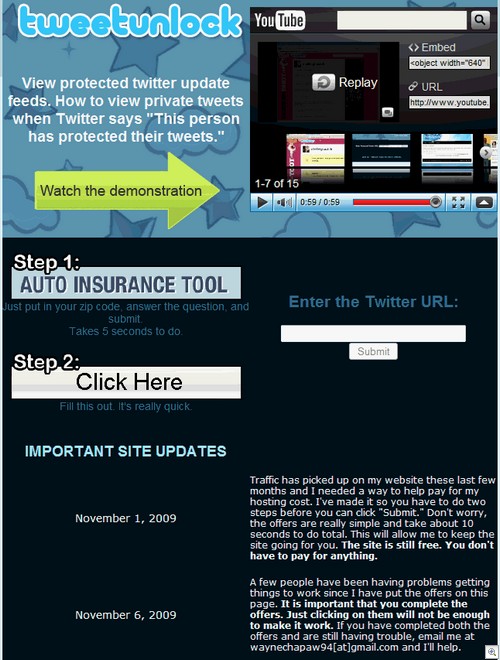
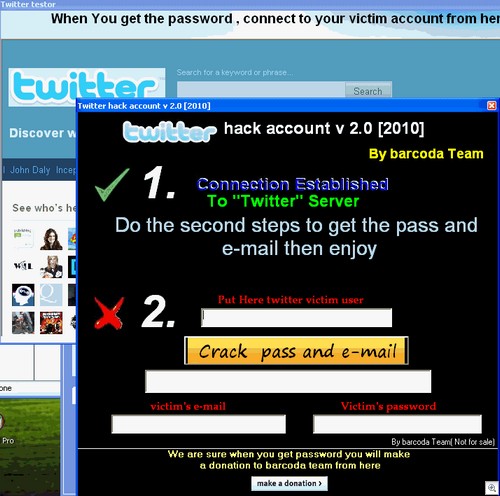
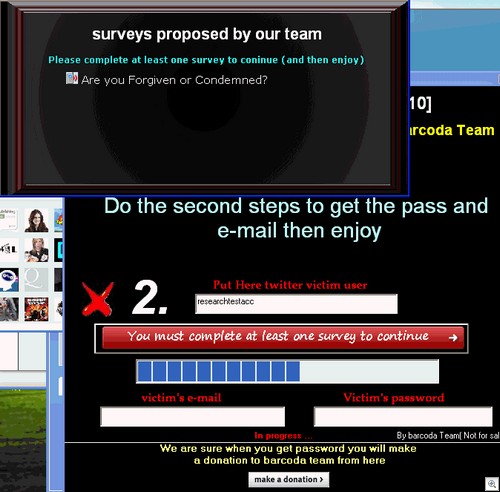
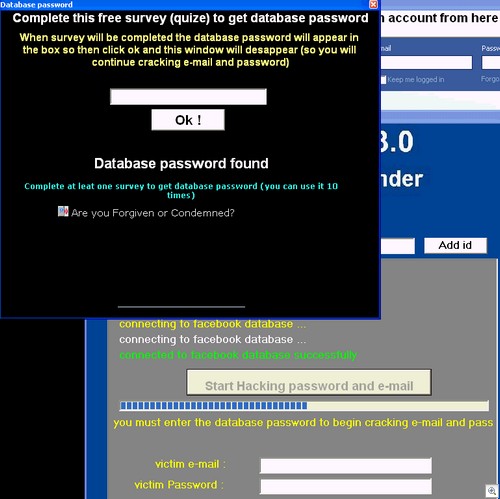
We just got an email from Dave Mook who is part of an effort to organize the Alliance of Qualified Malware Removal Boards (AQMRB).
Alliance membership will be free. Members will be reviewed every six months.
Boards in the alliance will have the right to display an official AQMRB badge:
Groups seeking membership must:
– Have been in existence for at least two years.
– Have an acceptable use policy and/or terms of use agreement
– Be on a paid hosting account.
– Have fully equipped/dedicated malware removal help and support section readable to all users and guests.
– Have malware removal staff who are trained by or have graduated from an acknowledged malware removal school or university
– Offer malware removal help free of charge for non-commercial users.
– Provide assistance to customers within 24 hours.of their post for help.
– Display no web links to illegal or copyright-protected software.
– Host no ads which will lead to malicious content.
– Not serve pop-ups or pop-under ads.
– Fill out an application and include a complete list of malware removal staff, including a list of the schools or universities where the staff received training.
Requests for alliance membership may be directed to the secretary of the alliance here: applications < at > aqmrb < dot > com.
Tom Kelchner