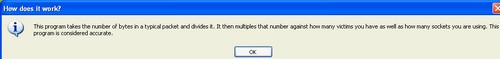
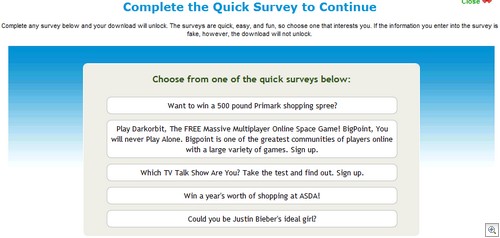
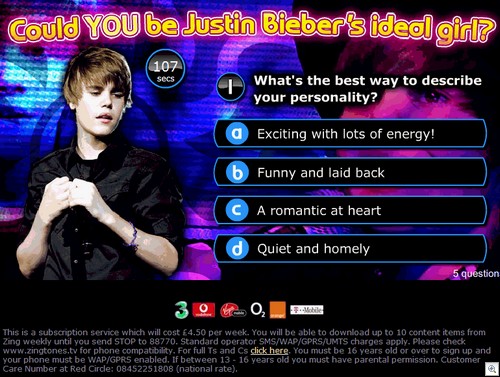
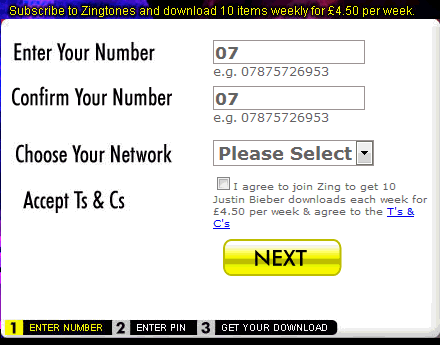
You can guarantee that everytime a new product comes out, someone will be offering a “free” version of it in return for filling in a survey.
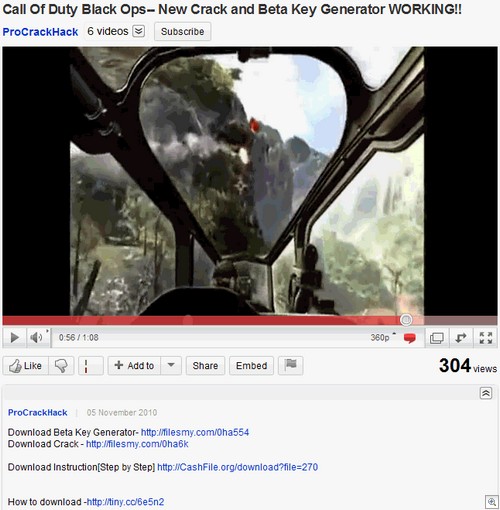
Yes, we’re all thoroughly sick of surveys. What caught my eye more than the entirely predictable “cracks” for Call of Duty Black Ops was a link sitting in most of the videos I saw:
“How to download”. Clicking that took me to scdownloads(dot)za(dot)pl, which actually gives the end-user step by step instructions on how to access files stored on “fill in a survey to download” sites such as Sharecash. Multiple languages, too!
I’ve no idea who created that website, but obviously individuals are so worried end-users won’t generate money for them that they’re resorting to giving us “The idiot’s guide” treatment. And that particular website isn’t limited to promotion in random fake crack videos, either – you’ll find it being linked to from all manner of offers, “freebies” and pilfered content:
Windows 7 mobile downloads, PS3 jailbreaks, MTV videos, shop hacks, Sony Vegas movie studio keygens…you name it, someone is doing their level best to have you fill in a survey with as little confusion as possible. I’m not entirely sure how “fill this in” could be confusing, but to give you an idea of the way that site is being linked to (and how popular links to surveys are on video sharing portals):

Youtube is telling me it has about 15,000+ links to the tutorial page, and there are fifty pages of links from the last day.
That’s fifty pages of links to surveys, garbage downloads and – of course – a wonderful tutorial ensuring end-users make the most out of getting nothing in return for signing personal information away.
Surveys: most definitely here to stay.
Christopher Boyd