We recently investigated a “Work from home” recruitment spam email. A trail of web links revealed an interesting labyrinth of sites peddling expensive “training” courses that suggest they can teach you can make huge amounts of money with very little effort.
And, while not being overtly illegal, they feature:
— disclaimers that say, in effect, everything on the page is fiction
— phony site-security certification seals
— blocked Whois information
For the inexperienced Web user who might be looking for a high-paying job, we’re going to walk through these sites and list eight clues that should make anyone suspicious.
The spam email
Yahoo! Mail
How would you like to make $75 hour working from home?
From: “Immediate Placement” ImmediatePlacement@hith757upfront.com
To: mailto: Undisclosed-Recipient@yahoo.com

(click to enlarge)
(A business advertised by spam email – this is your clue #1 that this should be avoided.)
The site
Clicking the link in the spam email (don’t try this at home) leads to:
http://www.workathomepositionplacement.com/index/

On the Work At Home Position Placement site “Elizabeth Jackson, America’s top work-at-home consultant” tells you in just 7,000 breathless words about how you can make $75 per hour posting merchandise on eBay, The (inferred) premise is that major companies are doing away with their bricks and mortar stores, selling on eBay and they need lots of people like you to work from home.
“All you have to do is spend a little time online cruising around eBay’s website, and you’ll soon see what I mean. Huge and successful companies like Apple, Coleman, Adidas and Compaq routinely list their products on eBay auctions…”
The cost of the training program: $197.
(A sales pitch that is too good to be true – this is clue #2 – with a lot of bold face type and colorful heads – clue #3)
Whois info is blocked
The Whois information for the domain is blocked. (clue #4) and the site has been registered only since April (clue #5). Legitimate businesses identify themselves and usually they’ve been in business (and had a domain registered) for more than a few days or weeks. Malicious or fraudulent sites are taken down quickly.
Domain name: workathomepositionplacement.com
Registrant Contact:
Whois Privacy Protection Service, Inc.
Whois Agent ()
Fax:
PMB 368, 14150 NE 20th St – F1
C/O workathomepositionplacement.com
Bellevue, WA 98007
US
Creation date: 07 Apr 2010 19:02:47
Expiration date: 07 Apr 2012 19:02:00
The site’s privacy policy lists what appears to be an attorney’s office in Henderson, Nevada.
Disclaimer
Disclaimers are a great view of the truth of the claims that these Web hucksters are making. They think they can skirt truth-in-advertising laws by drastically qualifying in their disclaimer everything they emphasize on their Web pages.
There is a disclaimer at the bottom of the Work At Home Position Placement Web page. It’s grayed out and clearly designed to be ignored (clue #6):

(click to enlarge)
You can cut and paste the text into a word processing application to make it readable. It’s interesting. Here are the highlights:
— “INCOME CLAIM WARNING: Testimonials are not typical of most results.”
— “All Testimonials are 100% Real and Accurate and the attestants have been remunerated for allowing Work At Home Position Placement’s use of the same.” (That means the “attestants” were paid for their testimonial.)
— “Photographs or images are a depiction of individuals and payment methods.” (That means the pictures with the testimonials are not of the people who SOLD their testimonials.)
— “Some individuals purchasing the program may make little or NO MONEY AT ALL.” (emphasis mine.)
— AND, Elizabeth Jackson isn’t even REAL: “For purposes of privacy, the creator of Work At Home Position Placement is using the name Elizabeth Jackson.” (We’re disappointed. She sounded so sincere.)
— “Work At Home Position Placement is not affiliated with, endorsed by or in any way associated with Apple, Coleman, Adidas, Compaq, The New York Times, Esquire, America Online, CNN, USA Today, Forbes, Yahoo. Work At Home Position Placement does not have the express permission of Apple, Coleman, Adidas, Compaq, The New York Times, Esquire, America Online, CNN, USA Today, Forbes, or Yahoo logo.” And that leads one to wonder why those logos are on the Work At Home Position Placement page. (Clue #7)
Security certifications?
The page uses the following graphics, which don’t seem to mean anything, but do leave the impression that there some kind of certification body approving their security/privacy policies/business (Clue #8):

Link to “training” site number two
A web searches for these “Web Guard” graphics above (with the unique file name wahr_order_webguard.jpg) leads to a second “training” site:
https://internetcareerbuilder.com/jobs/order2_files/wahr_order_webguard.jpg

Oddly, this site has the “Web Guard” graphics (above) on what appears to be an unused page and it carries other meaningless seals that state “Security Verified” and “Privacy Verified.”

They don’t link to any organization (the way legitimate certification seals do) and don’t offer any other information.
https://internetcareerbuilder.com/jobs/images/seals.gif
On InternetCareerBuilder.Com a visitor also is presented with:
“Special Report from Michelle Miller, the #1 work at home consultant in America”
Michelle’s pitch is just as wordy and enthusiastic as the fictitious “Elizabeth Jackson, America’s top work-at-home consultant” at workathomepositionplacement.com. And the cost of Michelle’s program: a familiar $197.
In the privacy policy, the site lists Las Vegas Navada, address:
Internet Career Builder
11136 Ferragamo CT
Las Vegas, NV 89141
Effective Date: August 25, 2009.
At least they didn’t deflate your enthusiasm by revealing that Michelle Miller is a fiction like Elizabeth Jackson just when you start to really like her.
Link to training site number three

Doing an image search for “seals.gif” – the “Security Verified” and “Privacy Verified” seals above oddly turns up the same graphic of the WebGuard seals on yet another “work from home” site:
http://www.auctiontrainingarea.com (caution)

Here the shill is “Joseph Delafont” and he wants you to know (in a succinct 5,800 words):

And the cost of the training is – you guessed it – $197.
The “earnings disclaimer” is in all caps and the central sentence:
“. . .WE DO NOT GUARANTEE OR IMPLY THAT YOU WILL WIN ANY INCENTIVES OR PRIZES THAT MAY BE OFFERED, GET RICH, THAT YOU WILL DO AS WELL, OR MAKE ANY MONEY AT ALL.”
The site’s Whois info is blocked
Administrative Contact:
Whois Privacy Protection Service, Inc.
Whois Agent (vkytynhr@whoisprivacyprotect.com)
+1.4252740657
Fax: +1.4259744730
PMB 368, 14150 NE 20th St – F1
C/O auctiontrainingarea.com
Bellevue, WA 98007
US
Creation date: 05 Dec 2008 23:37:17
Expiration date: 05 Dec 2010 23:37:00
The address listed on the bottom of the page:
Olympiad Inc – C/O Nisbetts Chamber, Charlestown, St Kitts
The disclaimer, however, claims:
“This Agreement shall be governed by and construed in accordance with the laws of Cyprus, without regard to its conflict of laws rules.”
Bogus security certifications can be very insecure

Interestingly enough, the “Web Guard” graphics on the sites we discussed are good imitations of the seals of a questionable “Trust Guard” certification provided by:
http://www.1automationwiz.com/trust-guard.html (only go there with caution.)

Which apparently nobody on the web has heard of and on Tuesday was infected with an iFrame Trojan: Trojan-Clicker.HTML.IFrame.fh (v)
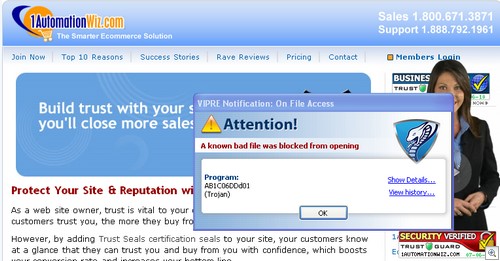
(click to enlarge)
Conclusion:
We’ve listed eight clues that let you know that this flavor of work-from-home-training scheme is probably not something you want to spend almost $200 for. Two of the sites, Work at Home Position Placement and InternetCareerBuilder, share most design elements and a probably a Nevada connection. Obviously they’re part of the same business. The third, AuctionTrainingArea which has the same graphic file on its site, is the same idea, possibly different owner.
And what about the bogus security certifications? Whoever designed the Work at Home Position Placement site obviously lifted the design of the certification graphics from 1automationwiz.com and that site either intentionally contains an iFrame exploit designed to download malware on your machine or has such bad security it got infected itself. That is not a “security” provider with any credibility.
Tom Kelchner