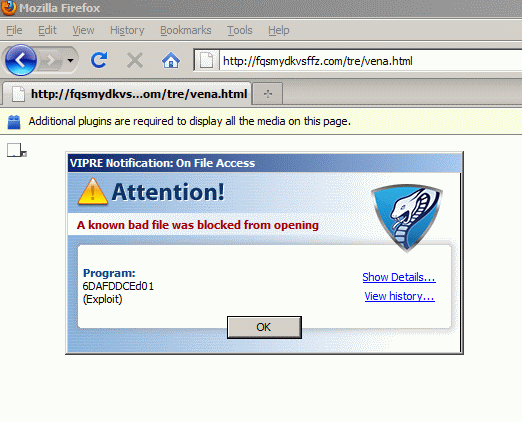
For a month or so now, support sites and Question / Answer services such as social.answers.microsoft and Yahoo Questions have been looking like this:
Two common themes: nobody seems to know where they get it from, and nobody can uninstall it. Out of all the threads posted, there seems to be only one that potentially gives some specifics with regards a possible source. If you don’t want to read his long ramble, here is his post in a nutshell:
“Went looking for Limewire, downloaded a version and now I have Tango Toolbar”.
So either he grabbed a cracked version which comes with the toolbar, or he downloaded something from P2P land which came with a few surprises. Regardless of infection route, it took a while to find the file in question because “It’s called Tango Toolbar and there’s a picture of a red hat on it” doesn’t really help much. The search was made more annoying by virtue of there being lots and lots of programs, skins and other things called Tango (or Tango Toolbar) that had nothing to do with this.
Things picked up a bit with this HijackThis log, listing a URL in the file which allowed me to grab a report from Threat Expert stuffed with the technical data I needed to pull the file from our database and have a play.
Shall we take a look? Presenting: The Tango Toolbar installer splash.

Click to Enlarge
I know what you’re thinking. However, despite the strangely similar name this doesn’t have anything to do with Zango. The splash claims it has a popup blocker, a built in search and offers “related keywords” when browsing. I particularly like the popup blocker, which notifies you of every popup blocked with the aid of a popup.
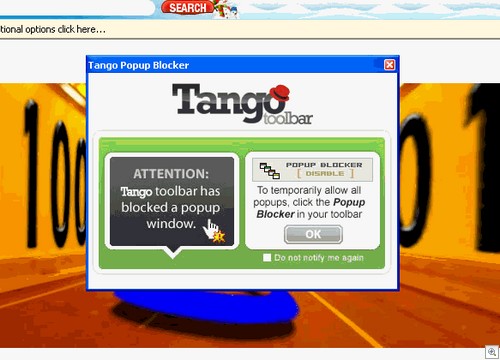
Click to Enlarge
I’m also a fan of the “Do not notify me again” checkbox, which works about as well as you’d expect. Three seconds later, and:
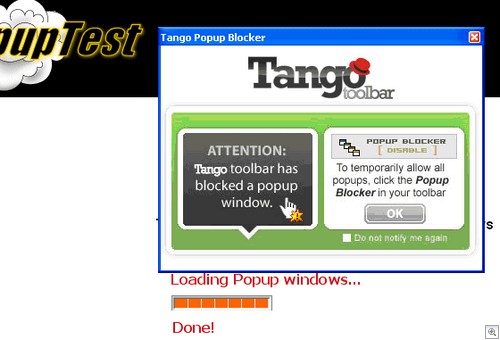
Click to Enlarge
Whoops.
The search results come from bar(dot)adbsearch(dot)com, and all seem to be sponsored. I didn’t see any inline adverts, but where this gets really interesting is when you try to uninstall. The “About” box makes it clear this toolbar has a EULA:
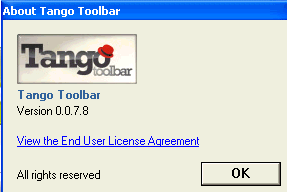
Clicking the link takes you to a site called gettango(dot)com:
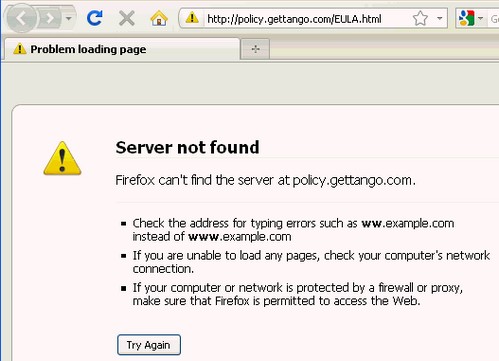
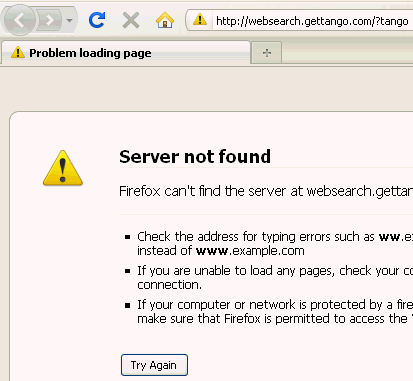
There is no EULA there, but the reason for this might be a little strange. See, gettango(dot)com is a site owned by a company called Brand Tango, who seem to be a marketing company dealing with timeshare/real-estate/hospitality. Can you see any connection between that and a random toolbar? Even stranger, if you go to Add / Remove Programs and attempt to uninstall this is what you’ll see:
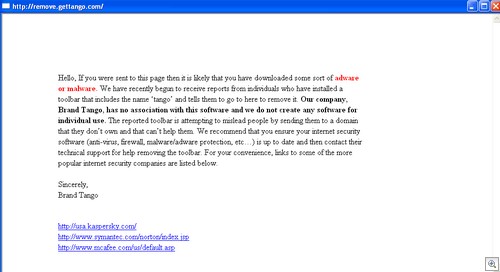
Click to Enlarge
A popup box with nothing other than a message served up from remove(dot)gettango(dot)com.
“Hello, If you were sent to this page then it is likely that you have downloaded some sort of adware or malware. We have recently begun to receive reports from individuals who have installed a toolbar that includes the name ‘tango’ and tells them to go to here to remove it. Our company, Brand Tango, has no association with this software and we do not create any software for individual use. The reported toolbar is attempting to mislead people by sending them to a domain that they don’t own and that can’t help them. We recommend that you ensure your internet security software (anti-virus, firewall, malware/adware protection, etc…) is up to date and then contact their technical support for help removing the toolbar. For your convenience, links to some of the more popular internet security companies are listed below.
Sincerely,
Brand Tango”
It then goes on to list Kaspersky, Symantec and McAfee as methods to remove the Toolbar. The Gettango domain and what appears to be their main website brand-tango(dot)com share similar domain registration data, and everything appears to be on the level. Is someone deliberately trying to mess with the reputation of Brand Tango by pointing a toolbar at their domains?
The secondary search feature accessed by clicking the Tango logo also points traffic to the gettango domain, too:
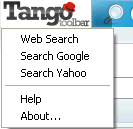
Interestingly, tangosearch(dot)com (from the HiJackThis logs) also has a message on their site:
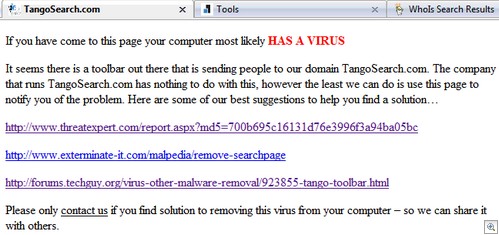
That site has different Whois data, showing as being “up for sale” and registered to hugedomains(dot)com.
It seems nobody wants anything to do with this toolbar, but it keeps crashing the party regardless. What we can say is that the toolbar is ultimately a problem for Mirar to resolve, even if registered through Domains By Proxy:

Click to Enlarge
This particular toolbar is a mess of broken uninstallers, disclaimers warding off associations with the product and endless people on support forums wondering how it ended up on their computers in the first place. In a situation such as this, there’s really only one course of action to take:
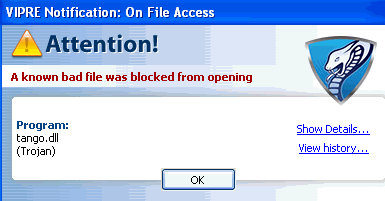
TANGO DOWN.
Christopher Boyd
(Thanks to Adam Thomas for additional research).