“…an unprecedented wave of Java exploitation” – Holly Stewart, Microsoft.
Bottom line: many Java exploits go after vulnerabilities that have been patched. Since Java runs on a wide variety of platforms, this makes it a very serious vector. You should stay alert for the automatic Java updates. You also can check the Java site (see link below.)
The background hum of news about the increase in malware that uses Java vulnerabilities has now increased to a roar.
Today Daniel Wesemann wrote a very readable blog post on the SANS site about Java weaknesses.
Wesemann pointed to an October piece on Microsoft’s Malware Protection Center by Holly Stewart in which she writes: “What I discovered was that some of our exploit ‘malware’ families were telling a scary story – an unprecedented wave of Java exploitation.”
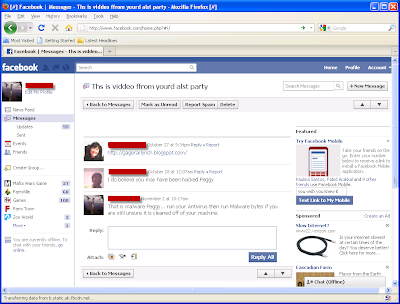
Wesemann described the method used by the recent “bpac” family of exploits. The Java vulnerability that it uses was patched in July he points out.
The infection usually happens as follows:
(1) User surfs to website that has been injected with the exploit
(2) Exploit pack triggers – it comes as an obfuscated JavaScript that downloads an (Java) Applet and a PDF
(3) The applet contains an exploit, here for CVE-2010-0840
(4) The applet is invoked with a parameter that tells it where to find the EXE
(5) If the exploit is successful, the EXE is downloaded and run”
And what is downloaded can be anything, like a back door that can steal your bank login information or turn your machine into a spam-pumping bot.
For beginners: Java is a compiled programming language created by Sun Microsystems (now owned by Oracle) that can be used to create applications that will run on a virtual operating system or in your browser. You may have heard of JavaScript. That is different. That is a scripting language that is put in the HTML code of web pages to run in your browser.
Here is Oracle’s description of the two:
What is JavaScript and how is it different from Java Technology?
The JavaScript programming language, developed by Netscape, Inc., is not part of the Java platform.
JavaScript, does not create applets or standalone applications. In its most common form today, JavaScript resides inside HTML documents, and can provide levels of interactivity to web pages that are not achievable with simple HTML.
Listed are key differences between the Java and JavaScript.
* Java is an object oriented programming (OOP) language while Java Script is an OOP scripting language.
* Java creates applications that run in a virtual machine or browser while JavaScript code is run on a browser only.
* Java code needs to be compiled while JavaScript code is all in text.
* They require different plug-ins.
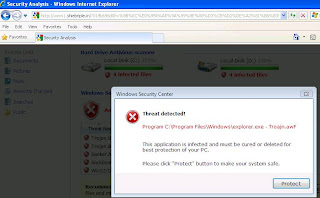
How to check to see if your machine needs updates
To test your machine to see if the latest version of Java is installed, go to this test link with your browser: http://www.java.com/en/download/help/testvm.xml
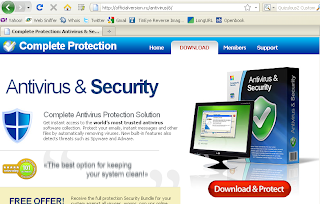
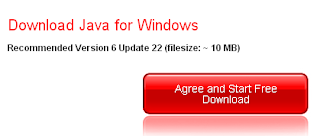
If your Java installation is out of date, you will see something like this:
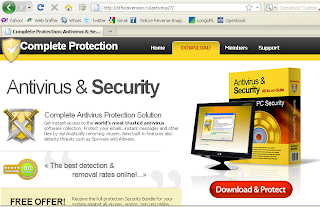
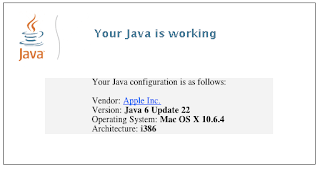
If you have the current version, you will see something like this:
Tom Kelchner