I don’t want your heads to explode with the force of a thousand Suns, but I think we may be looking at a new Rogue AV gimmick – specifically in the area of Codecs. I know, I know. Breathe deeply and take a seat.
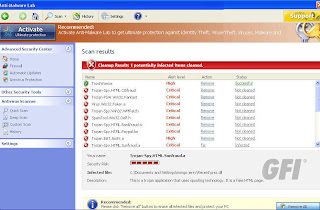
Researcher Adam Thomas was investigating some FakeVimes Rogues, installing one of the fake products from the usual “Your PC has been infected” website:
Click to Enlarge
He then got ready to take in the sights when this happened: nothing.
No fake security tool asking for payment or telling you the PC has about a million fictitious infections on it, no flashing lights, nothing at all. He rebooted the test machine – still nothing (sometimes a rogue won’t rise from the depths until you restart the machine. Surprise!)
This is a typical FakeVimes GUI:
Click to Enlarge
This is not a typical FakeVimes GUI:
Click to Enlarge
You can see what I did there. Anyway, this is a sample of some of the files found on the infected machine:
c:Documents and SettingsAll UsersApplication Data7f0924VD7f0_2326.exe
c:Documents and SettingsAll UsersApplication Dataipe.exe
c:Documents and SettingsAll UsersApplication DataipFRed32.dll
c:Documents and SettingsAll UsersApplication Dataipinstr.ini
c:Documents and SettingsAll UsersApplication DataipSmartGeare.exe
c:Documents and SettingsAll UsersApplication Dataipspoof.avi
c:WINDOWSsystem32c_726535.nls
Adam went off to the main folder where all the nasty things reside, and found something interesting lurking:
Click to Enlarge
“Spoof.avi”? Well, hello there. Let’s see what you get up to in your spare time:
Click to Enlarge
A “Your Codec version is too old” message, complete with popup in the bottom right hand corner telling you to “Update your Codec”.
Is this FakeVimes variant designed to prevent you watching movies while making the creator some cash into the bargain? Let’s take a look. Opening up a random website to view some files gave some interesting results.
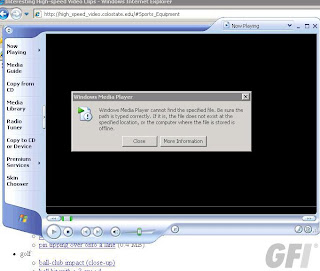
This is what happened when Adam downloaded a video and tried to play it:
Click to Enlarge
“Windows Media Player cannot find the selected file”.
Not to be beaten, he tried to stream the file instead. Then they schooled us with science. And a large popup.
Click to Enlarge
“Your player cannot display this video file. Click here to update the Codec”.
At this point, you might be expecting infection files, but you’re already infected. So what are they going to do?
This:
Click to Enlarge
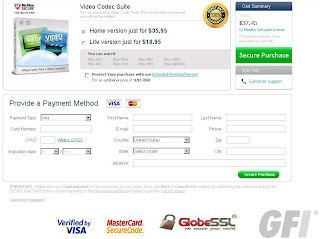
“Home Codec pack and video converter suite: This version contains a full package of codecs enabling you to watch video in the best quality possible”.
Yes, and my name is Elvis. Hitting the (extremely large) Purchase buttons will give you this “Show me the money” payment screen, asking you for up to $35.95 for the “Home” version, plus an optional $9.95 to “Protect your purchase” with an extended download service:
Click to Enlarge
Call it a hunch, but I think the best optional extra here is to run in the opposite direction from this particular fiasco. Of course, it makes sense for the people behind these attacks to start mixing things up a little – FakeVimes has been all over the news recently, and not in a “We love you, FakeVimes” kind of fashion. More like a “FakeVimes, we hate you and we want you to die” fashion as Google took the unprecedented step of warning millions of infected users about it last week. From the Google help page on this one:
A warning appears at the top of the search results page when we believe that the computer you’re using is infected with malicious software, also known as “malware.” Malware can be used to intercept your computer’s connection to Google and other sites. When Google’s system detects that a connection has been intercepted, it’s likely that the computer was previously infected with malicious software.
With the heat coming around the corner, the FakeVimes people have decided to diversify into a sort of “Rogue Codec” market instead, and it looks like things could be interesting in Rogue AV land for a while as their otherwise glacier-like tactics (“You’re infected, have some Rogue AV, thanks for the money”) begin to change.
We detect this one as VirTool.Win32.Obfuscator.hg!b (v).
Christopher Boyd (Thanks to Adam Thomas for finding this one)