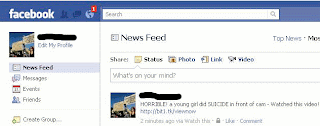
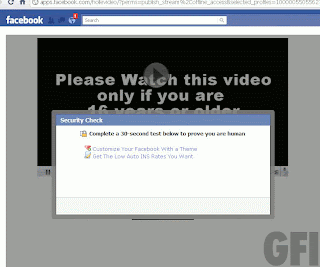
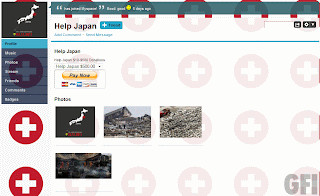
Thanks to the person who sent this over but wishes to remain anonymous – appreciated!
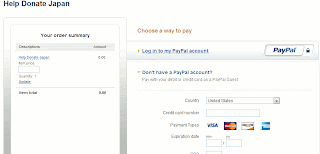
Below, we have a rather interesting twist on the 419 scam mail (and of course, it’s related to the Japanese Earthquake / Tsunami). They don’t ask you to jump onto a phish page and sign your life away – instead, they ask you to send your information to the actual Red Cross but also ask you to CC whatever you send to their alternate scam email address.
Seeing as how the Red Cross will probably take a while to get back to you while in the middle of dealing with the Japanese disaster relief, by the time they’re asking you why you sent them endless emails involving Western Union money transfers the 419 scammer has probably cleaned out your bank account.
Here comes the mail, with important bits highlighted in bold:
From: British Red Cross(Donation Board) [mailto:relieffortsATredcross.org.uk]
Subject: Donate to Japan Tsunami Relief Efforts
British Red Cross
Japan Tsunami Appeal
British Red Cross
44 Moorfields
London
EC2Y 9AL
The massive earthquake and resulting tsunami that struck Japan on 11
March have caused widespread destruction and suffering, relayed on
television screens around the world.
More than 4,300 people have died in the disaster, thousands are
injured or missing, and more than 440,000 people have had to leave
their homes.
The British Red Cross has already deployed 11 disaster-response teams
with medical personnel providing medication, food items, blankets,
clothing and many more relief assistance to the Tsunami victims in
Japan.
Similar to its efforts in the aftermath of the Haiti Earthquake, the
Red Cross is accepting donations online.
We hereby appeal to you individuals, public, families and companies,
to assist us with an online fund raising to enable us treat and render
our services to over one million people affected with the tsunami
disaster across Japan.
Help give shelter to the homeless in Japan, treatment to the injured,
cloths, food items, blankets and many more to the needy here in Japan.
No amount of donation is small; send us your donation in London, UK
through Western Union Money Transfer for amounts less than $10,000 USD
and for amounts above the $10,000 USD, on your request account details
shall be provided.
If you cannot assist us financially, you can also help by forwarding
this message to all your friends and contacts.
We will have the names of our donors appeared in our relief magazines
and websites on their approval while there will be space for photos,
names and business adverts for company donors in our
magazines/websites on their approval.
Donations should be made via any of the following means;
– Western Union Money Transfer
– Direct deposit into Correspondent Bank Account (For donations above
$10,000 USD)
We shall provide you with our payment details and directives upon the
confirmation of your desired means.
Kindly send us your Names and Phone Number so we can reach you for
further information on how to assist the needy in Japan.
Note: Whenever you send us an email, endeavor to CC every message to
our alternate email address: uk.redcross@blumail.org in any case our
spam filters reject your messages.
Sincerely,
British Red Cross
Email: relieffortsATredcross.org.uk
Alternate: uk.redcrossATblumail.org
Pretty clever. As always, don’t reply to blind mailshots asking for your information even when it appears to be totally legitimate.
Christopher Boyd