Update: Looks like we’re all clear — the searches have been cleaned-up.
.
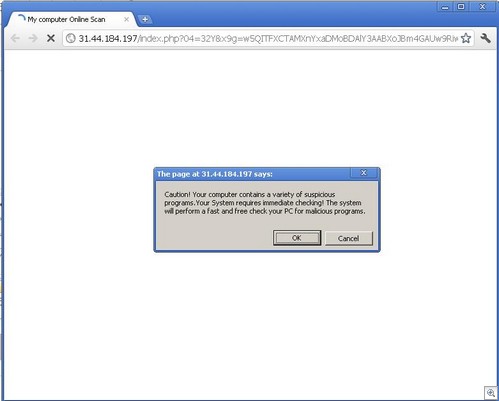
The Microsoft Safety and Security Center has become a hot bed of porn redirects, and sleazy porn sites invariably lead to malware.
And there’s an interesting twist to how this occurred. Search poisoning, on its own, is no big deal. But in this case, something else is going on.
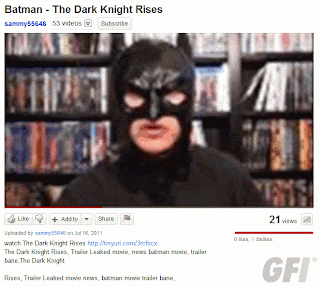
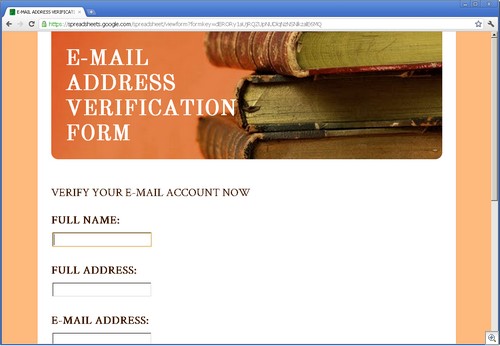
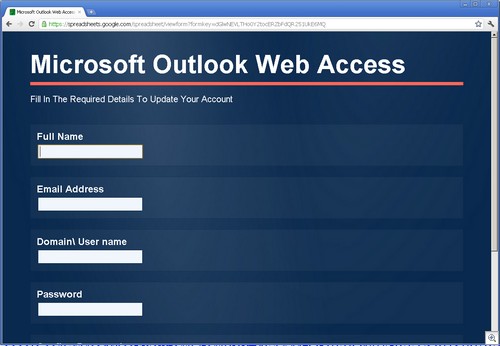
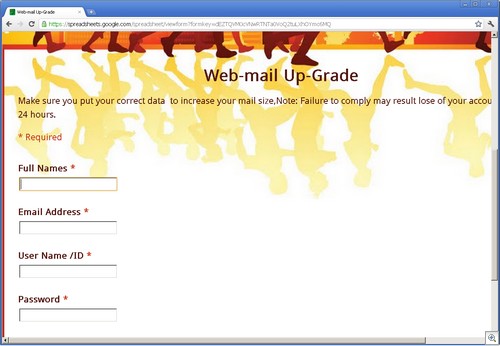
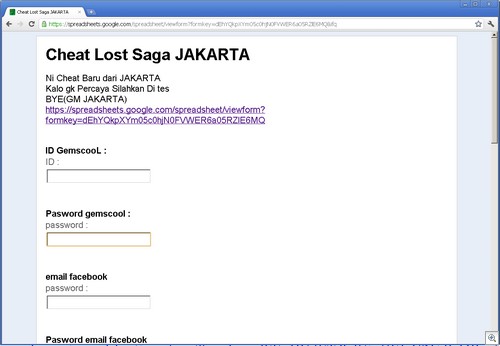
Since we’re a (sort of) PG 13 blog, I’ll give a mundane example: A person goes to the Microsoft Safety and Security center and types in “girl” in search box.
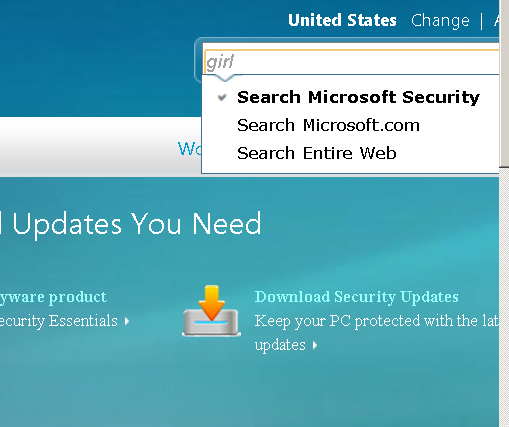
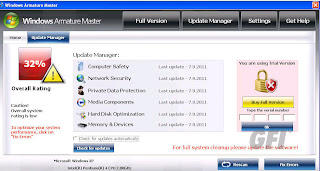
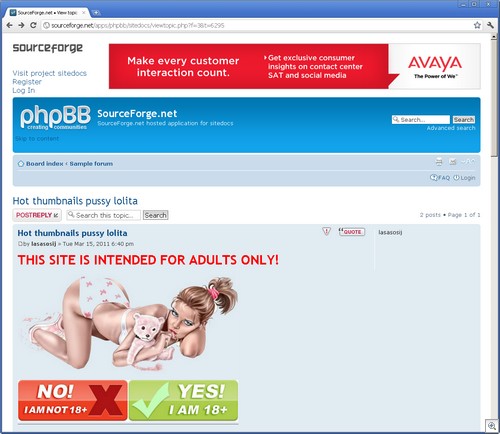
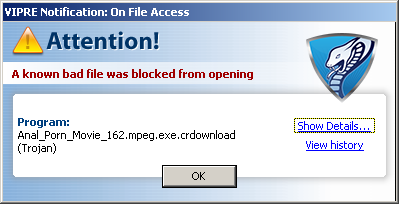
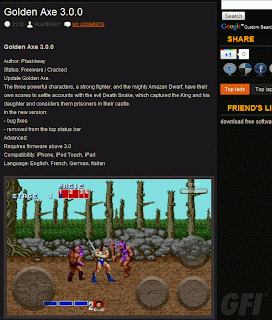
The search results have been poisoned. Even an innocous search such as this one returns nasty results (don’t click on the thumbnail if you’re offended by foul language):
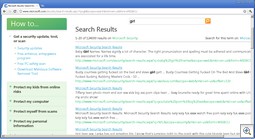
(Searching for porn terms will yield some very nasty results. Most of the stuff is far too disturbing to post on this blog.)
Interesting SEO blackhatting: Why is this different? Normal search poisoning is where results come up that directly link to a site. However, blackhat SEOs have created Microsoft Security Center search results on specific terms. These terms include things like:
porn
you porn
free porn
free filipino porn video
prnhub
streaming
you tube sex
And even: “baby girl names”
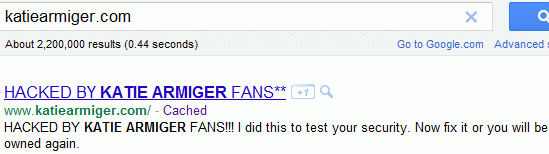
You can see this with a Google search on microsoft.com:
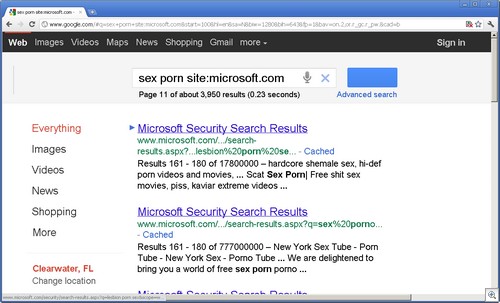
(It’s ironic that only Microsoft Safety and Security Center searches are returning porn results. Nothing else at Microsoft.)
Since only specific terms are used, if you search using a different term, say “united nations”, you’ll get real, normal results.
In other words, blackhat SEOs are seeding illegimate search results within the Microsoft search results. Pretty tricky and impressive. There are a number of ways this could be done (for example, using the ability on the site to Twitter a search result).
Confused? You don’t need to be. Just know that inevitably, these types of things can lead to malware.
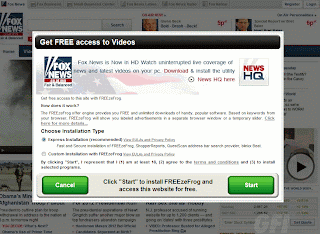
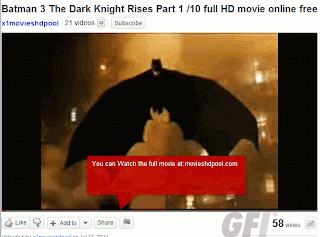
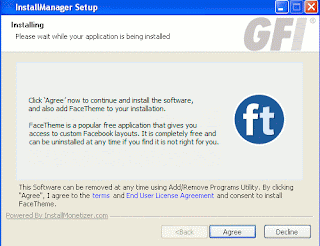
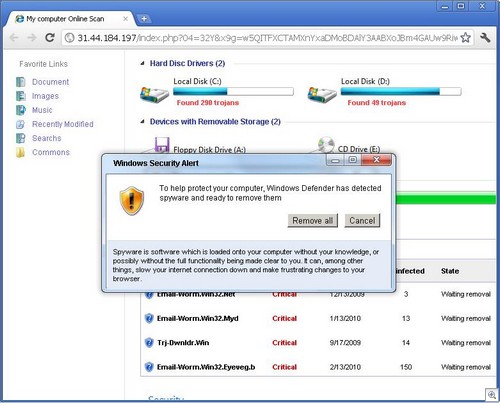
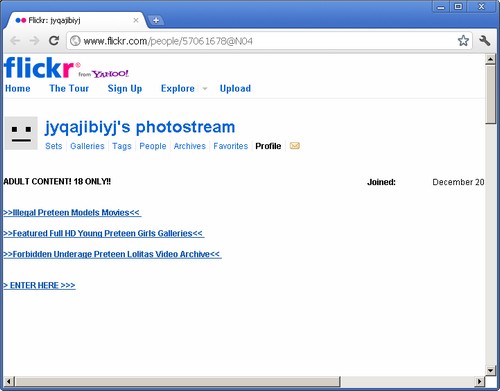
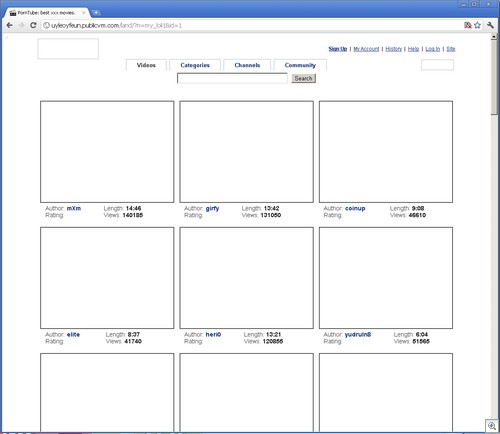
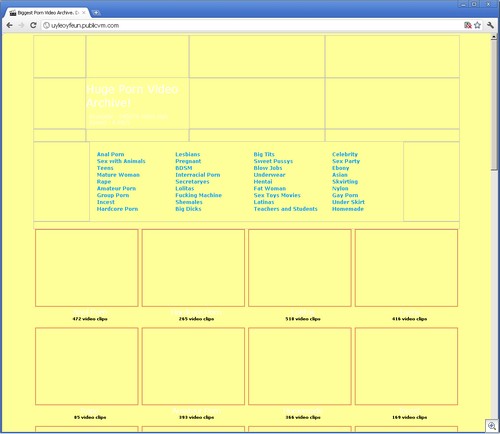
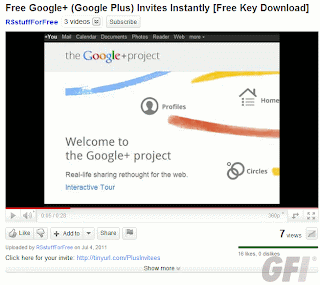
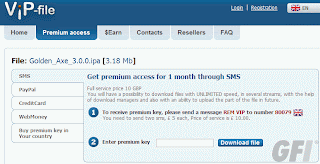
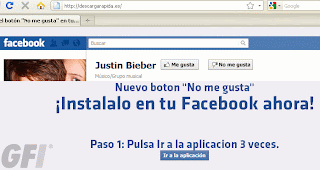
Just a bit of hunting around on the search results, and you might find something like this:
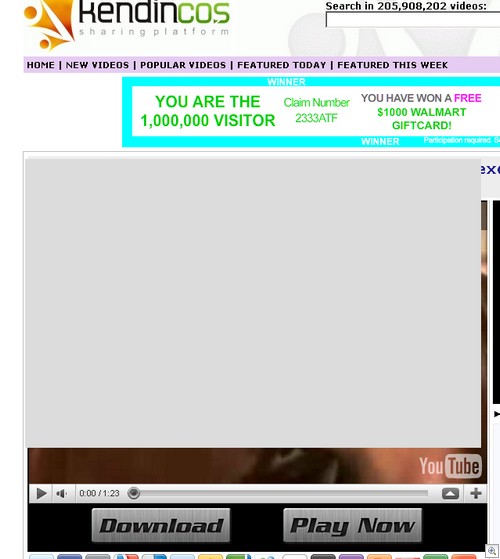
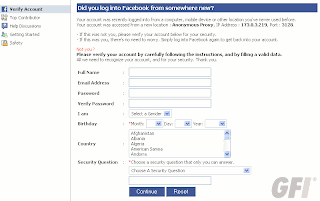
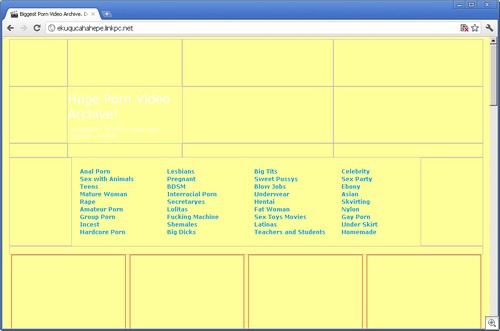
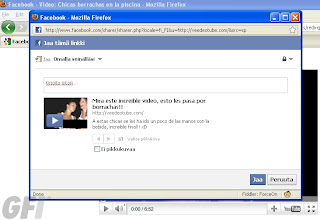
And pressing download gets you to a fake codec site, which pushes malware:
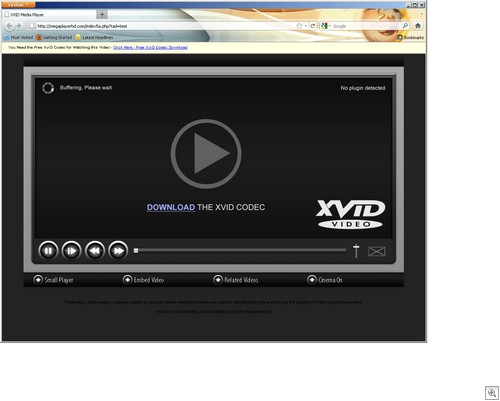
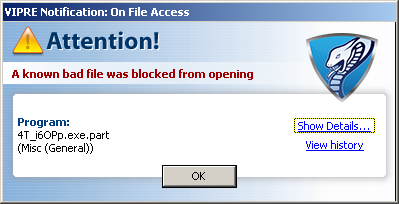
It’s Zugo,a Bing-branded search toolbar with a history of being installed through exploits and other misleading/deceptive means. It’s a a rather poetic twist of irony (unrelated to the search story here), that Zugo is a Microsoft Bing partner.
At any rate, let’s hope this all gets cleaned up soon…
Alex Eckelberry
(Hat tip to Patrick Jordan)