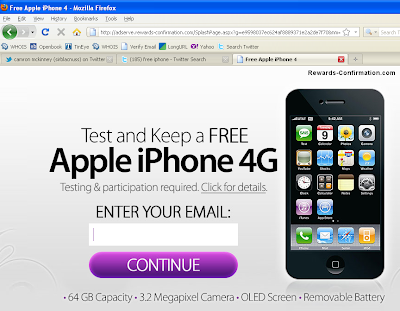
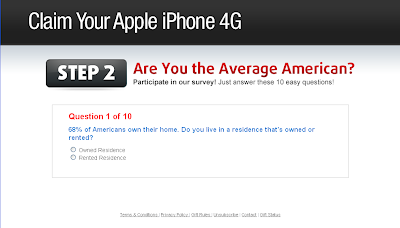
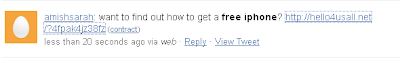
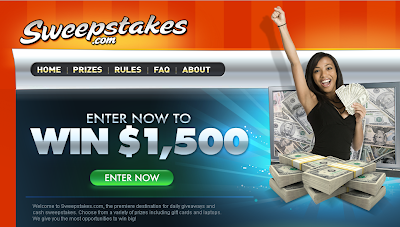
Today, it’s all about the taco.
Not those nice things wrapped in tortilla – another kind of taco, served up from an evil fast food joint of doom.
And by “evil fast food joint”, I mean “slightly rubbish website asking you to install things”.
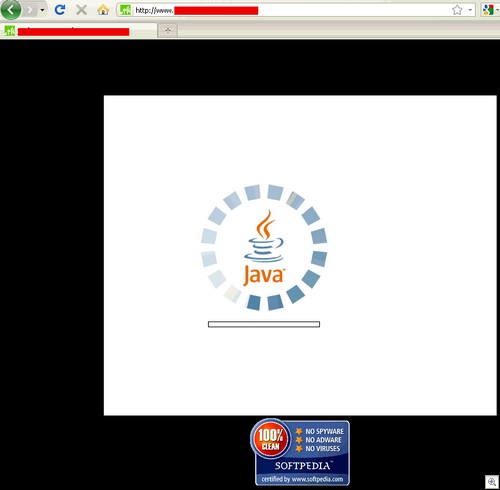
It is, of course, one of those fake Java install websites that pop up from time to time – complete with (fake) Softpedia 100% clean notice. I think the last time I saw one of these was back in April of last year.
This one does exactly the same thing – pops up a prompt asking the user to hit “Run” on a Java notification. When that happens, a rather generic Trojan named after one of my favourite nibbles swings into action.
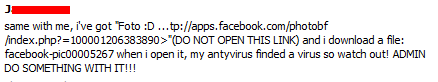
Say hello to the Taco:

Insanely high detection levels ensure this particular Taco won’t be causing any PC indigestion. However, good advice never goes out of fashion:
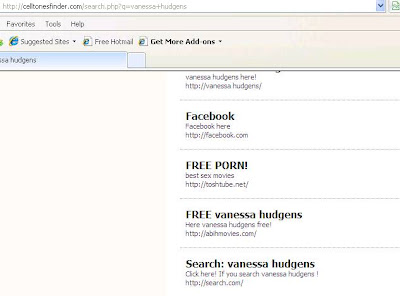
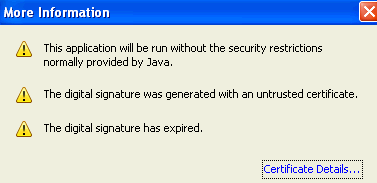
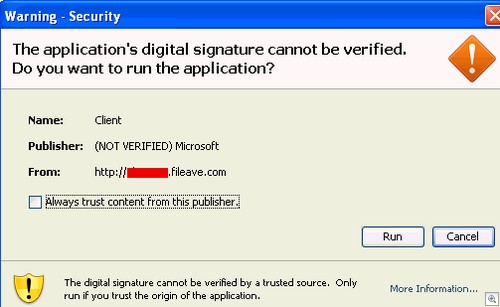
Hey look, it’s being served up from Fileave.com, a host for random files that anybody can upload. Looking legit so far. I particularly like the “NOT VERIFIED” next to Microsoft. Hitting the “More information” box should set those final alarm bells ringing:
Yeah…you know what? I think I’ll skip the taco and buy some oranges instead.
I’ll finish this one off with some cut and paste action from an earlier writeup:
* ALWAYS be cautious when presented with an unknown application. Don’t just run it; go Google it first and see if anyone else even mentions it.
* In the same spirit, be very wary of unsigned applications on random websites you’ve never heard of.
* Anyone can grab an award badge from a website and claim they’re the “Best thing ever”.
Don’t eat out tonight.
Christopher Boyd


 Andreas Marx at
Andreas Marx at